Investigating Windows
-
Whats the version and year of the windows machine?
Answer : windows server 2016
-
Which user logged in last?
Write a little powershell script lastloguser.ps1 :
$com=read-host "Enter Computer name here"
Get-WmiObject -Class Win32_NetworkLoginProfile -ComputerName $com |
Sort-Object -Property LastLogon -Descending |
Select-Object -Property * -First 1 |
Where-Object {$_.LastLogon -match "(\d{14})"} |
Foreach-Object { New-Object PSObject -Property @{ Name=$_.Name;LastLogon=[datetime]::ParseExact($matches[0], "yyyyMMddHHmmss", $null)}}
Execute and enter the Hostname of the computer at prompted : EC2AMAZ-I8UHO76 :
./lastloguser.ps1
Answer : Administrator
-
When did John log onto the system last?
Answer format: MM/DD/YYYY H:MM:SS AM/PM
Using "net user" command :
C:\Users>net user john | findstr "log"
Last logon 3/2/2019 5:48:32 PM
Answer : 03/02/2019 5:48:32 PM
-
What IP does the system connect to when it first starts?
Let's check a particular registry entry for start up actions :
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
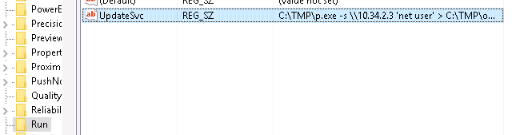
Answer : 10.34.2.3
-
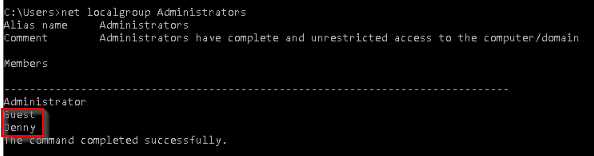
What two accounts had administrative privileges (other than the Administrator user)?
Answer format: username1, username2
Checking the local Administrator group with net command :
Answer : Jenny, Guest
-
Whats the name of the scheduled task that is malicous.
Open the task scheduler then looking around the few tasks. One of them seems suspect with it's name : "Clean file system" so i looked its actions tab :
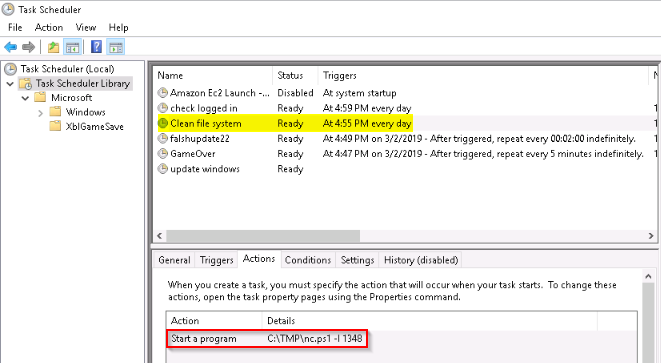
This task is launching a netcat listener to open port 1348
Answer : Clean file system
-
What file was the task trying to run daily?
As we can see on above screenshot, this task launch a powershell script : nc.ps1
Answer : nc.ps1
-
What port did this file listen locally for?
As we can see on above screenshot too, the listening port is 1348
Answer : 1348
-
When did Jenny last logon?
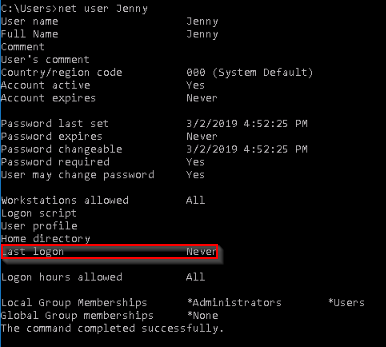
Answer : Never
-
At what date did the compromise take place?
Answer format: MM/DD/YYYY
The suspects elements in the C:\TMP folder are all dated from 03/02/2019 :
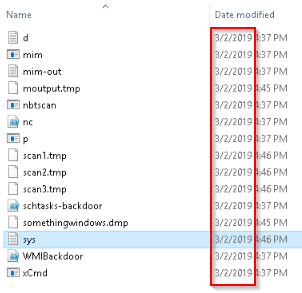
Answer : 03/02/2019
-
At what time did Windows first assign special privileges to a new logon?
Answer format: MM/DD/YYYY HH:MM:SS AM/PM
I searched for the "Special privileges" Windows Event ID and found 4672 on Microsoft documentation.
Looking around the time of the attack, the first event is :
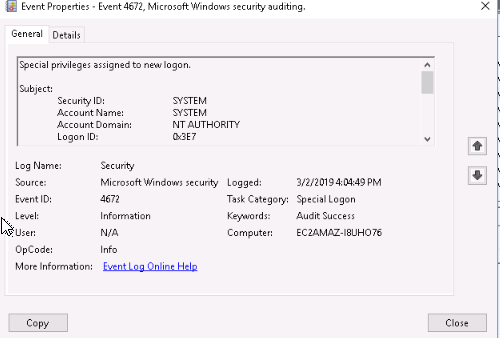
Answer : 03/02/2019 04:04:49 PM
-
What tool was used to get Windows passwords?
Looking at mim-out.txt :
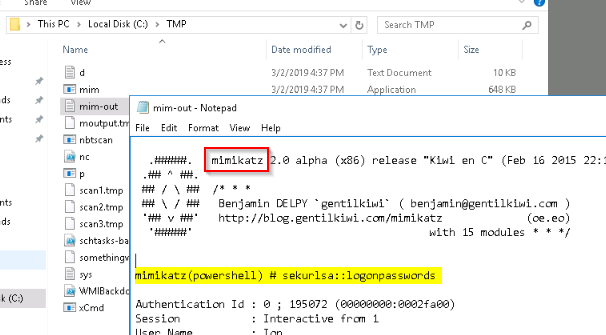
Answer : mimikatz
-
What was the attackers external control and command servers IP?
Looking for redirection of dns traffic in the hosts windows file :
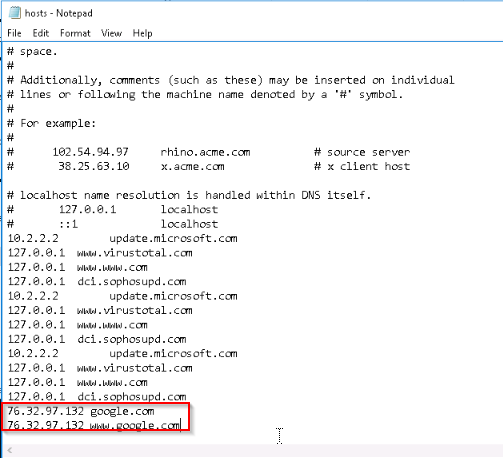
Answer : 76.32.97.132
-
What was the extension name of the shell uploaded via the servers website?
The windows server website (IIS) has content stored in C:\inetpub\wwwroot :
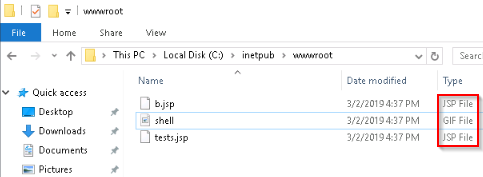
Answer : .jsp
-
What was the last port the attacker opened?
In order to communicate with the Control and Command Server (see question above) the hacker had set up a firewall rules :
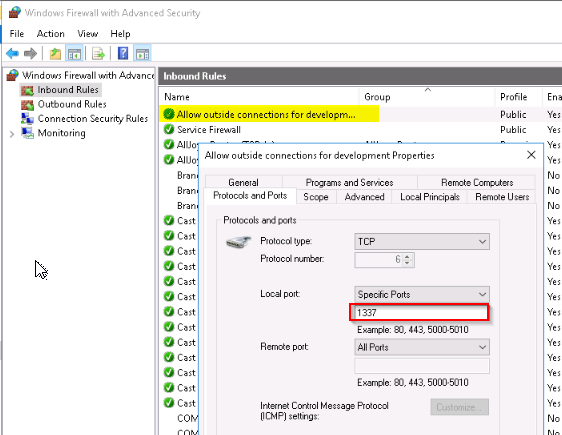
Answer : 1337
-
Check for DNS poisoning, what site was targeted?
DNS record can be manage in the Windows Hosts file :
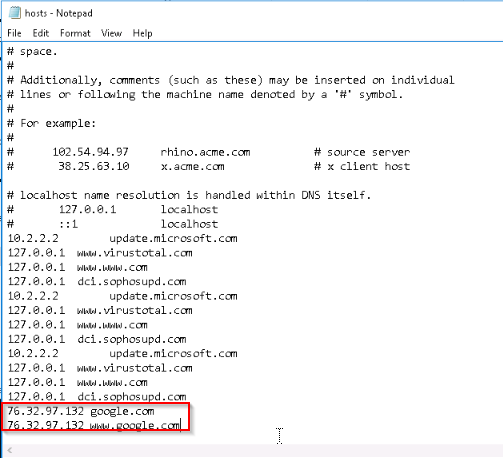
Answer : google.com