Splunk 101
THM Room https://tryhackme.com/room/splunk101
-
Virtual machine deployed.
No Answer
-
I'm ready to look at Splunk apps.
No Answer
-
What is the 'Folder name' for the add-on?
Install the app on the desktop : splunk-add-on-for-microsoft-sysmon_1062.tgz then navigate to the apps :
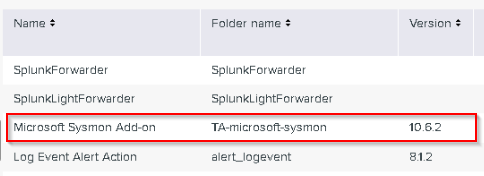
Answer : TA-microsoft-sysmon
-
What is the Version?
Answer : 10.6.2
-
Upload the Splunk tutorial data on the desktop. How many events are in this source?
Upload >zip file on desktop > next > submit > search
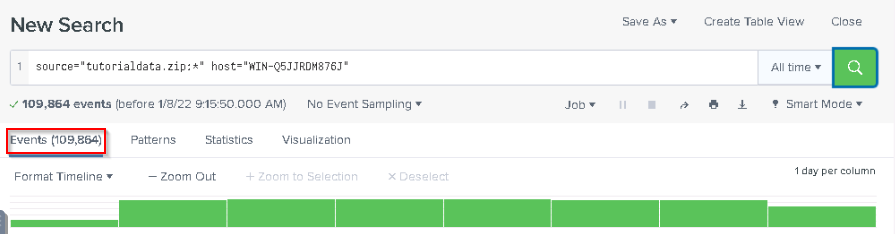
Answer : 109,864
-
Use Splunk to Search for the phrase 'failed password' using tutorialdata.zip as the source.
No Answer.
-
What is the sourcetype?
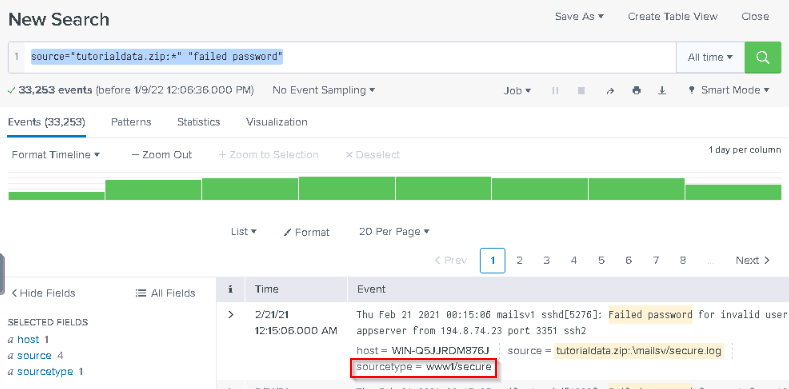
Answer : www1/secure
-
In the search result, look at the Patterns tab.
No Answer.
-
What is the last username in this tab?
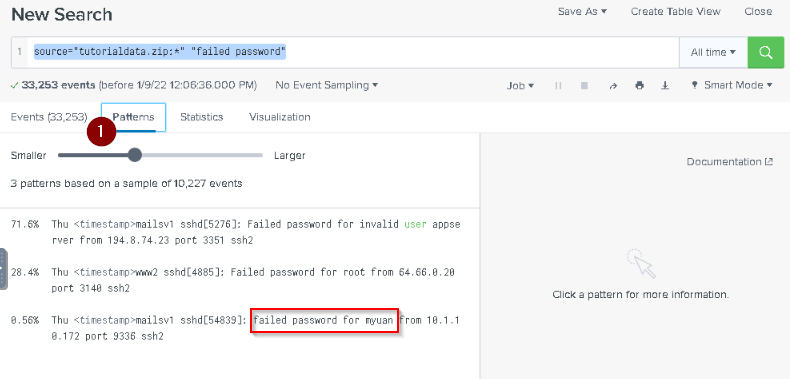
Answer : myuan
-
Search for failed password events for this specific username. How many events are returned?
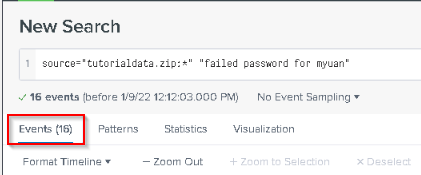
Answer : 16
-
Use the Select document feature. What is the Splunk query for 'sigma: APT29'?
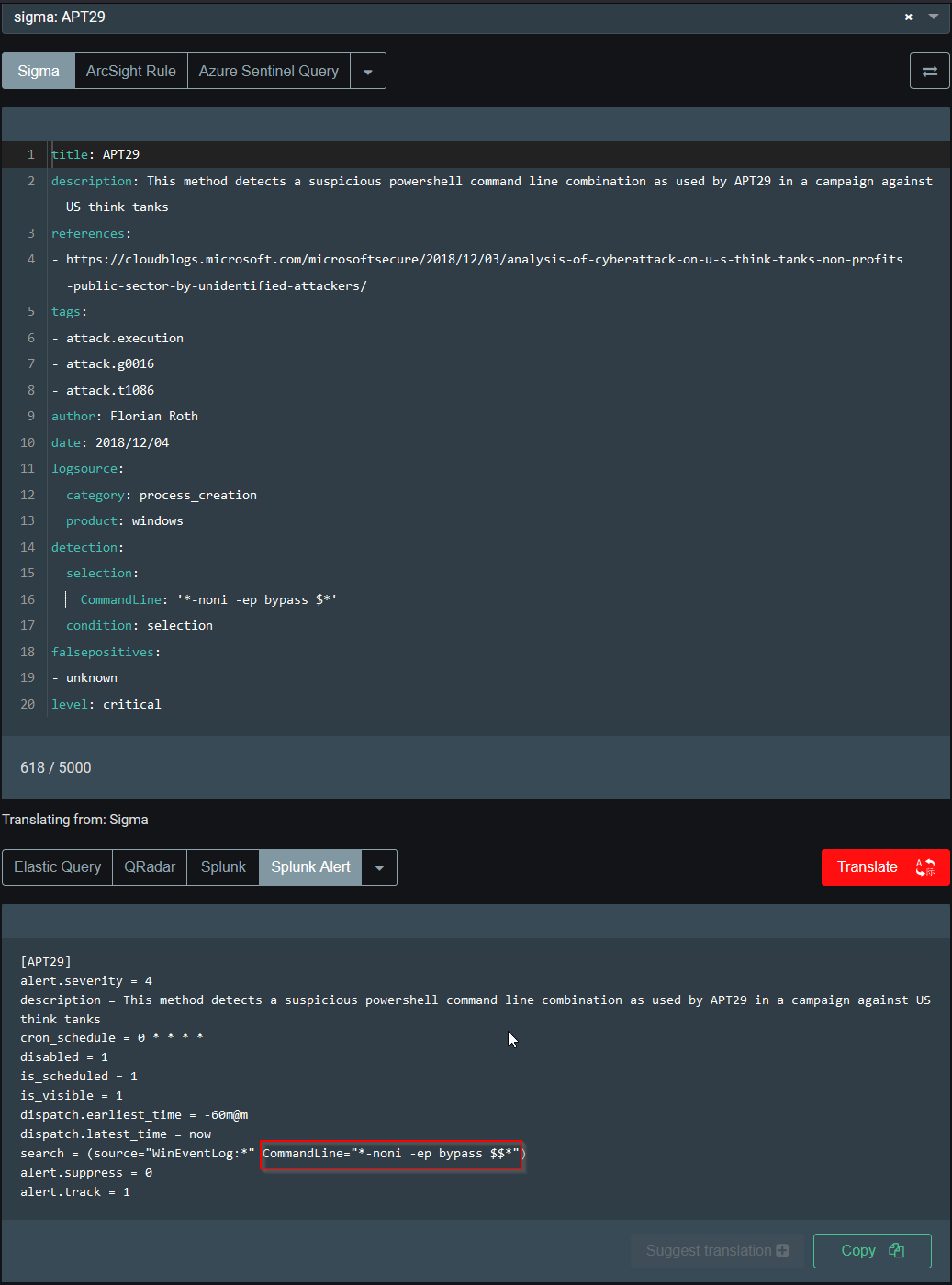
Answer : CommandLine="*-noni -ep bypass $$*
-
Use the Github Sigma repo. What is the Splunk query for 'CACTUSTORCH Remote Thread Creation'?
By the hint : Check the Windows rules. Copy and paste into uncoder.io.
GO to this repo in the windows part related to thread : https://github.com/SigmaHQ/sigma/tree/master/rules/windows/create_remote_thread
Then copy the code of "sysmon_cactustorch.yml" into encoder.io to translate the rule in splunk.
Answer : (source="WinEventLog:*" (SourceImage="*\\System32\\cscript.exe" OR SourceImage="*\\System32\\wscript.exe" OR SourceImage="*\\System32\\mshta.exe" OR SourceImage="*\\winword.exe" OR SourceImage="*\\excel.exe") TargetImage="*\\SysWOW64\\*" NOT StartModule="*")
- What is the highest EventID?
Answer : 11
-
I have a general understanding on how to create an alert in Splunk.
No Answer.
-
I know the fundamentals of Splunk.
No Answer.