Burp Suite: Other Modules
-
Deploy the machine attached to this task !
No Answer
-
Familiarise yourself with the Decoder interface.
No Answer
Base64 encode the phrase: Let's Start Simple. What is the base64 encoded version of this text ?
URL Decode this data: %4e%65%78%74%3a%20%44%65%63%6f%64%69%6e%67. What is the plaintext returned ?
Answer : Next: Decoding
Use Smart Decode to decode this data: %34%37 . What is the decoded text ?
Answer : 47
Encode this phrase: Encoding Challenge. Start with base64 encoding. Take the output of this and convert it into ASCII Hex. Finally, encode the hex string into octal. What is the final string ?
Encoding Challenge > RW5jb2RpbmcgQ2hhbGxlbmdl > 5257356a62325270626d6367513268686247786c626d646c > 24034214a720270024142d541357471232250253552c1162d1206c
Answer : 24034214a720270024142d541357471232250253552c1162d1206c
-
Using Decoder, what is the SHA-256 hashsum of the phrase: Let's get Hashing! ? Convert this into an ASCII Hex string for the answer to this question.
Let's get Hashing! > kr5qõ¯V0KYlµut7âyP r#¾ > 6b72350e719a8ef5af560830164b13596cb582757437e21d1879502072238abe
Answer : 6b72350e719a8ef5af560830164b13596cb582757437e21d1879502072238abe
-
Generate an MD4 hashsum of the phrase: Insecure Algorithms. Encode this as base64 (not ASCII Hex) before submitting.
Insecure Algorithms > MÅx@fY7¼»DÃ(x > TcV4QGZZN7y7lwYFRMMoeA==
Answer : TcV4QGZZN7y7lwYFRMMoeA==
-
Now read the problem specification below:
"Some joker has messed with my SSH key! There are four keys in the directory, and I have no idea which is the real one. The MD5 hashsum for my key is 3166226048d6ad776370dc105d40d9f8 -- could you find it for me?"
Submit the correct key name as your answer.
MD5(Key1) = µ#祴è*%O&iäj|*
ASCII_hex(µ#祴è*%O&iäj|*) = b523e7a5b4e82a254f2669e46a7c012a
MD5(Key2) = _´Ç<Á¬ÃPúåöeU
ASCII_hex(_´Ç<Á¬ÃPúåöeU) = 915fb4c73cc1acc350fae502f6655500
MD5(Key3) = 1f"`HÖwcpÜ]@Ùø
ASCII_hex(1f"`HÖwcpÜ]@Ùø) = 3166226048d6ad776370dc105d40d9f8
Answer : key3
-
Familiarise yourself with the Comparer interface.
No Answer
-
Navigate to http://10.10.189.188/support/login
Try to login with an invalid username and password -- capture the request in the Burp Proxy.
No Answer
-
Send the request to Repeater with Ctrl + R (or Mac equivalent), or by right-clicking on the request in Proxy and choosing to "Send to Repeater".
No Answer
-
Send the request, then right-click on the response and choose "Send to Comparer".
No Answer
-
In the Repeater tab, change the credentials to:
Username: support_admin
Password: w58ySK4W
Send the request again, then pass the new response into Comparer.
No Answer
-
Compare the two responses by word. How many differences does Comparer detect in total ?
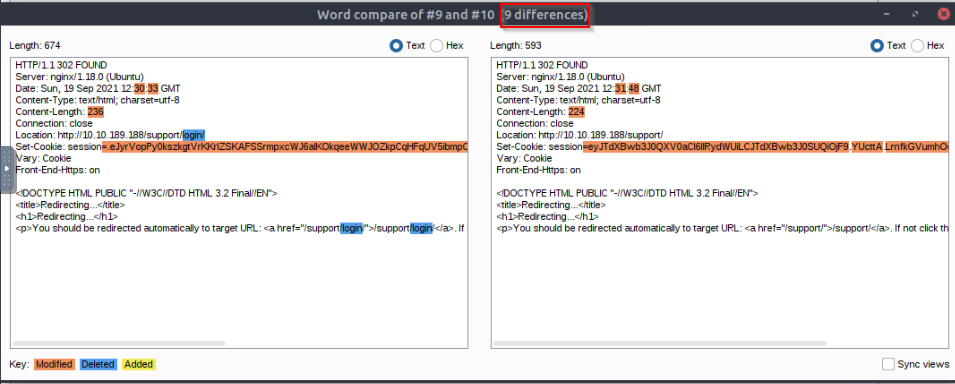
Answer : 9
-
Familiarise yourself with the Live capture and Manual load interfaces. We will be looking more in-depth at the Live capture interface in the next task.
No Answer
-
Follow the steps above to perform entropy analysis on the loginToken set by the /admin/login route of our target web app.
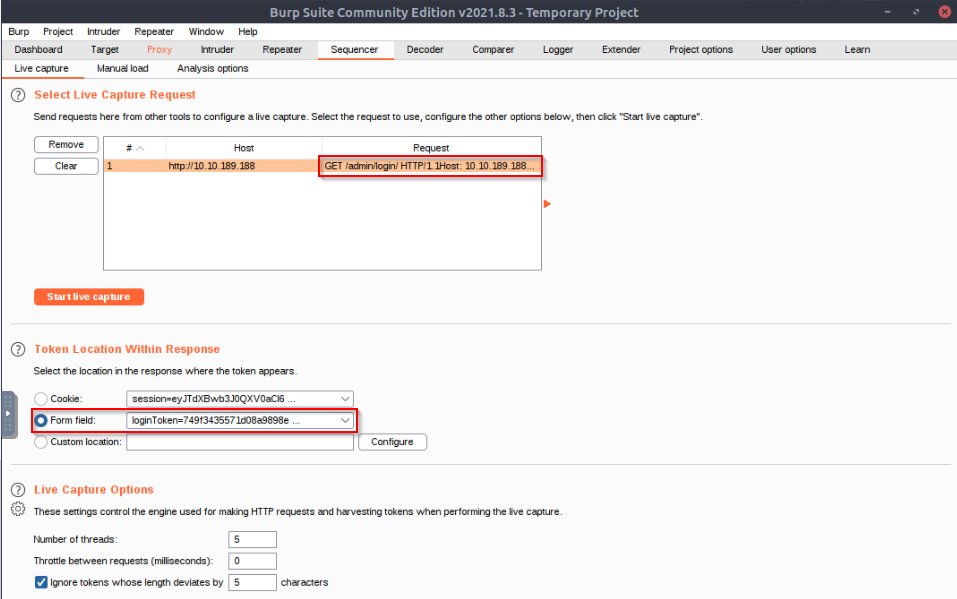
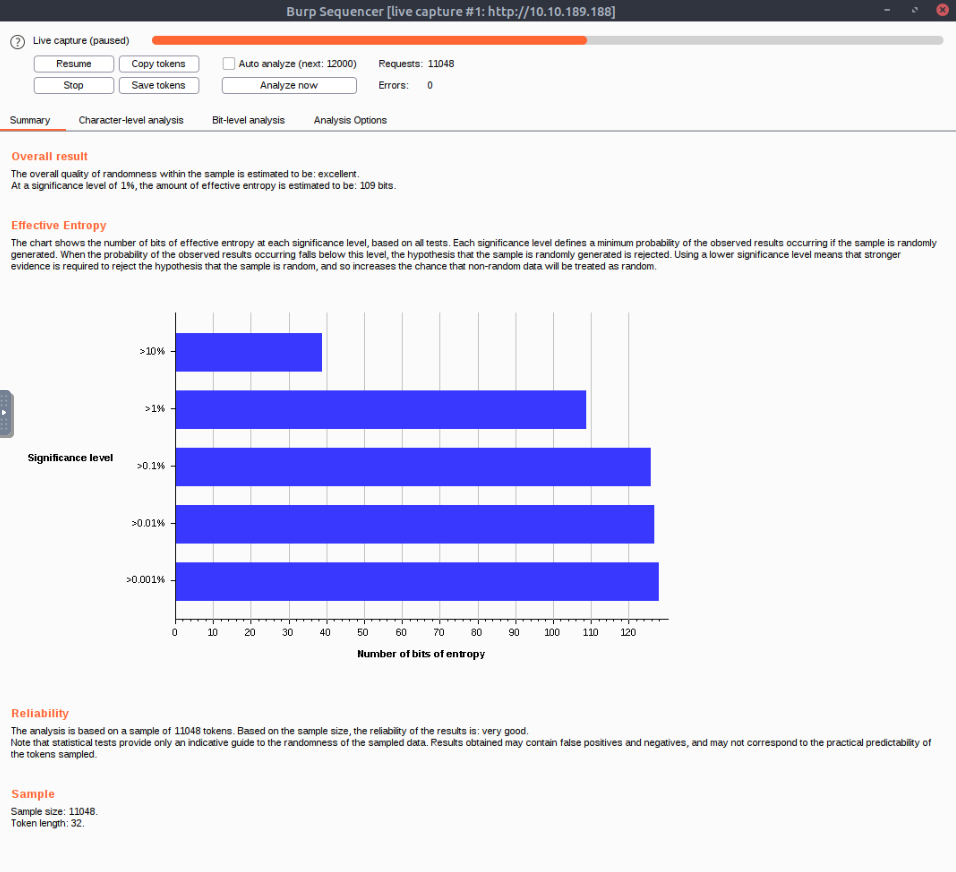
No Answer
-
[Bonus Question -- Optional] Try performing the capture again, but this time monitor your requests in Wireshark. Can you see why live capturing the requests for this analysis can be described as "loud"?
No Answer
-
Take some time to look through the tests that Burp used to generate its summary. You don't need to understand all of these, but it is important to know that they exist.
No Answer
-
I understand how to use Decoder, Sequencer, and Comparer!
No Answer