Common Attacks
-
Let's get started!0
No Answer
-
Read the task information and watch the attached videos
No Answer
-
What was the original target of Stuxnet?
Answer : the Iran nuclear programme
-
Click the green "View Site" button at the top of this task if you haven't already done so.
No Answer.
-
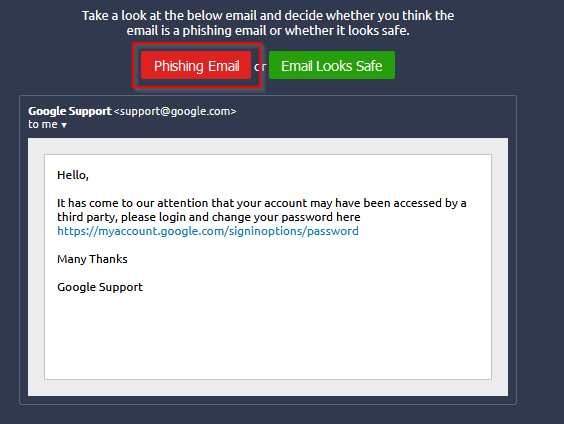
What is the flag?
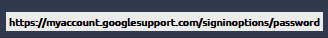
First phishing/safe email, link and showed-link are different :
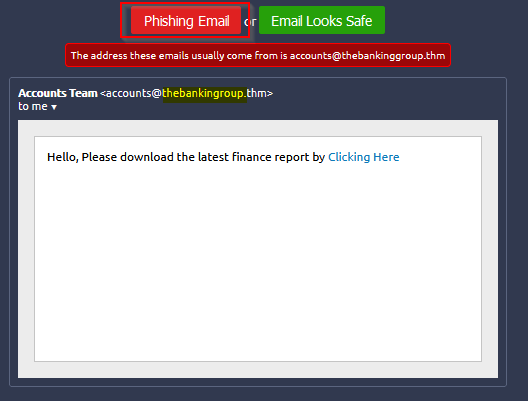
Second one is phishing too. Misspelling in the email address and suspicious attachment ;
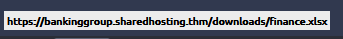
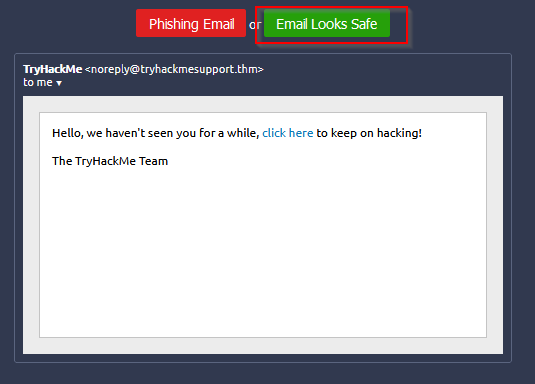
Third one is safe :

And last one is phishing because of file attachment from untrsuted sender or not expected :
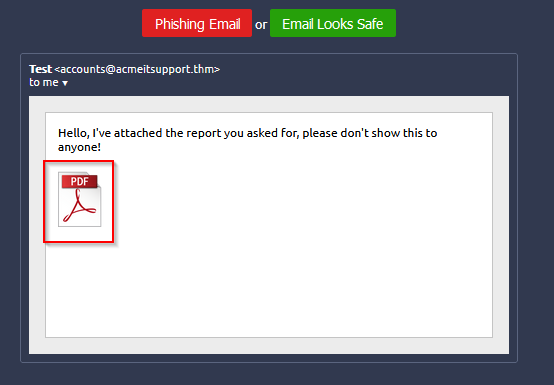
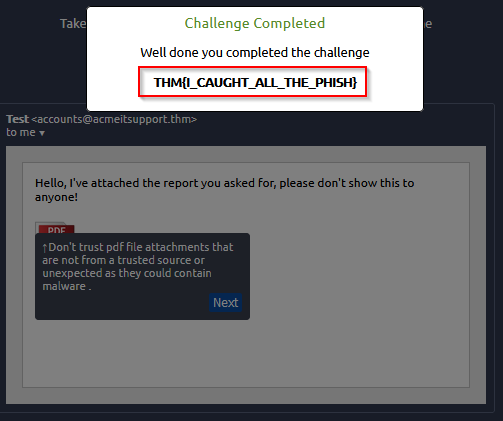
Answer : THM{I_CAUGHT_ALL_THE_PHISH}
-
[Research] What currency did the Wannacry attackers request payment in?
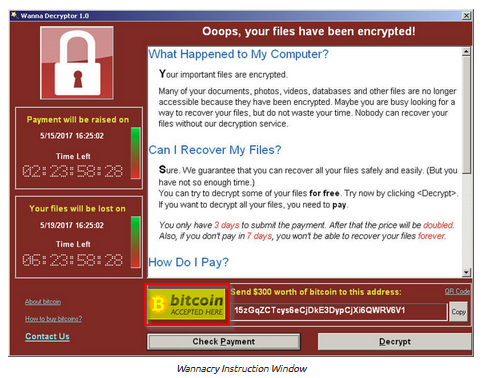
Answer : bitcoin
-
Put yourself in the shoes of a malicious hacker. You have managed to dump the password database for an online service, but you still have to crack those hashes! Click the green button at the start of the task to deploy the interactive hash brute-forcer!
No Answer.
-
Copy the list of passwords into the "Password List" field of the hash cracker, then click "Go"!
No Answer.
-
The hash cracker should find the password that matches the target hash very quickly.
What is the password?
Putting password list in the box, all MD5 will be computed and compared to the real password MD5 :
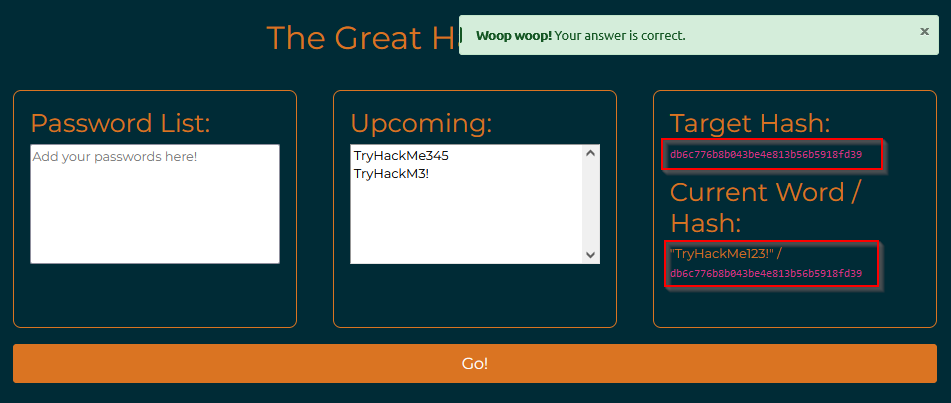
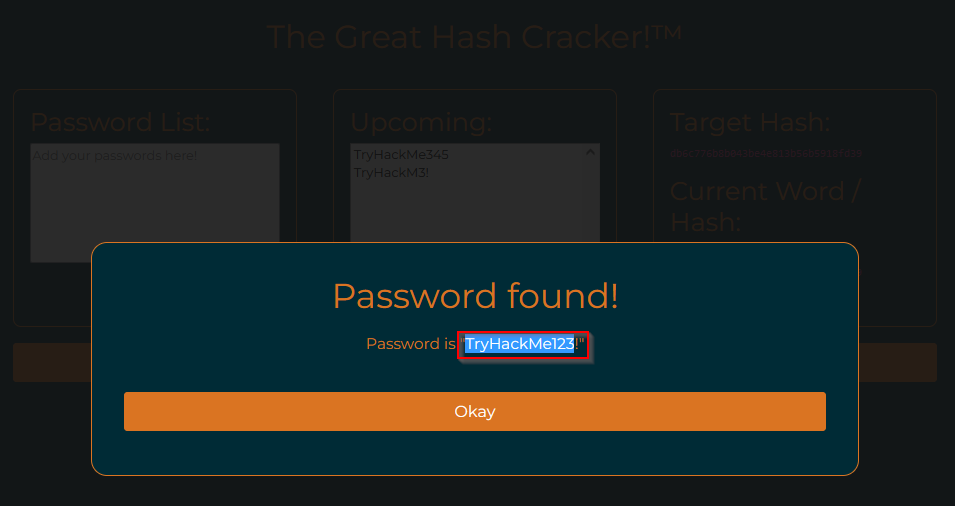
Answer : TryHackMe123!
-
In the next task we will look at some of the common account protection measures, as well as how to generate secure passwords.
No Answer.
-
Where you have the option, which should you use as a second authentication factor between SMS based TOTPs or Authenticator App based TOTPs (SMS or App)?

Answer : APP
- Deploy the interactive content by clicking the green button at the top of the task.
No Answer.
-
The interactive content for this task demonstrates what can happen if information is sent over a potentially unsafe network with various types of encryption (or lack thereof). There is no flag for this task, but you are encouraged to try each of the different scenarios, mixing and matching the options provided in the control box at the bottom right of the screen.
No VPN nor HTTPS :

HTTPS without VPN :
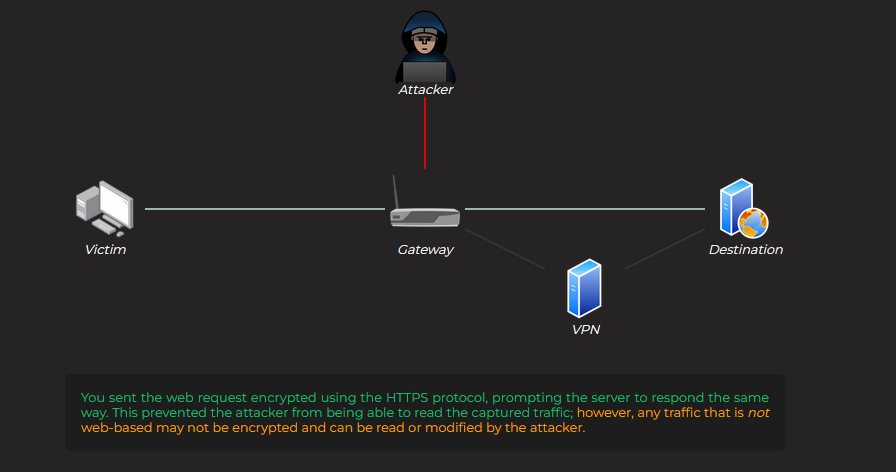
VPN without HTTPS :
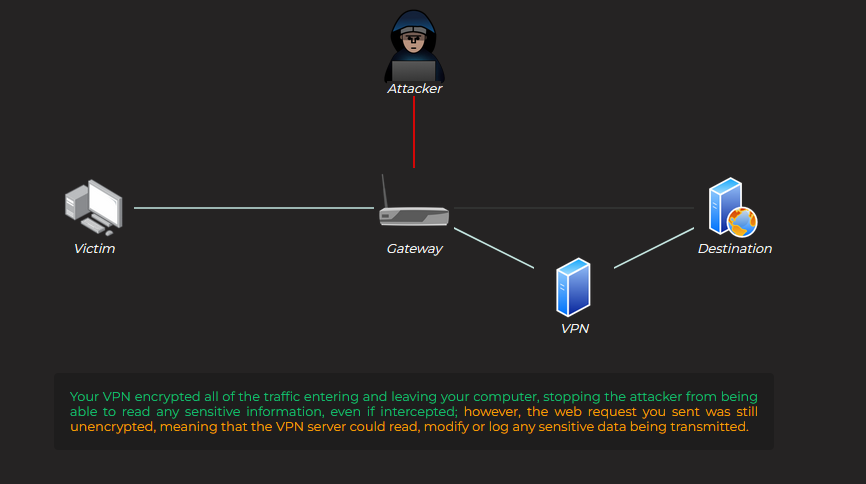
VPN and HTTPS :
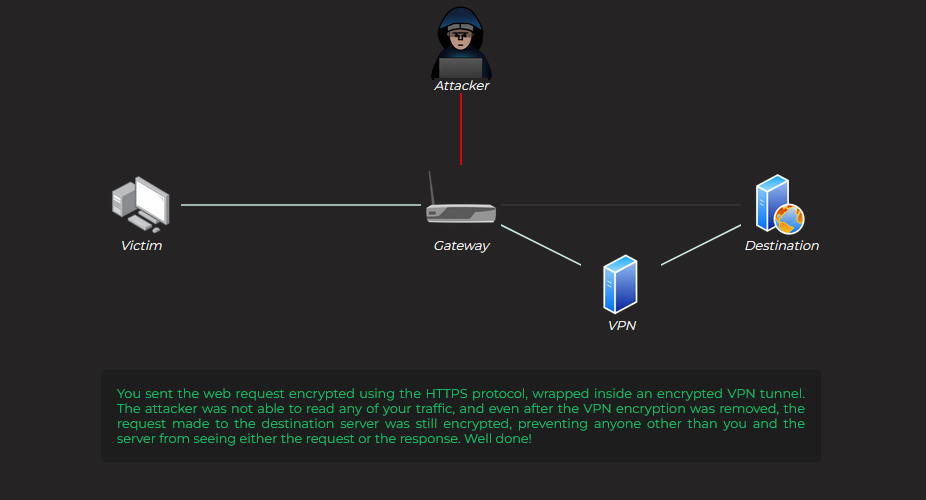
No Answer.
-
What is the minimum number of up-to-date backups you should make?
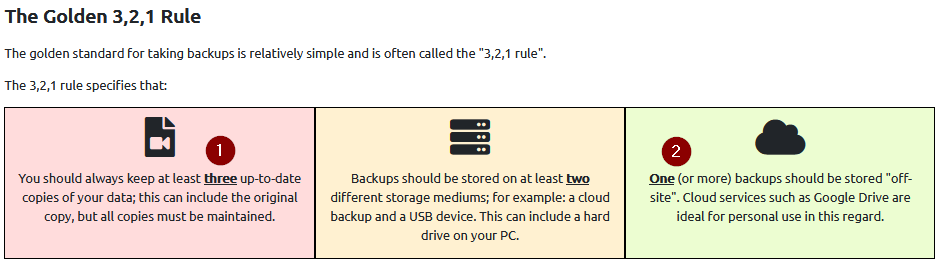
Answer : 3
-
Of these, how many (at minimum) should be stored in another location?
Answer : 1
- (Optional) Complete the Blue room on TryHackMe to see the brutal effects of the Eternal Blue exploit in action against an unpatched machine for yourself!
-
I have completed the Common Attacks room!
No Answer.