MAL: Malware Introductory
-
Ah, now I kinda understand...
No Answer
-
What is the famous example of a targeted attack-esque Malware that targeted Iran?
Just googling the info if you don't remember it ! Per Wikipedia :
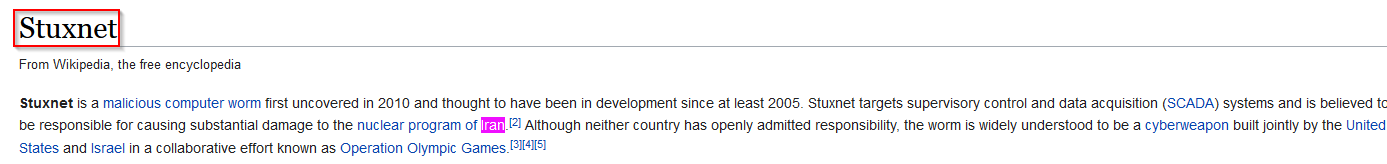
Answer : Stuxnet
-
What is the name of the Ransomware that used the Eternalblue exploit in a "Mass Campaign" attack?
Idem, per Wikipedia :
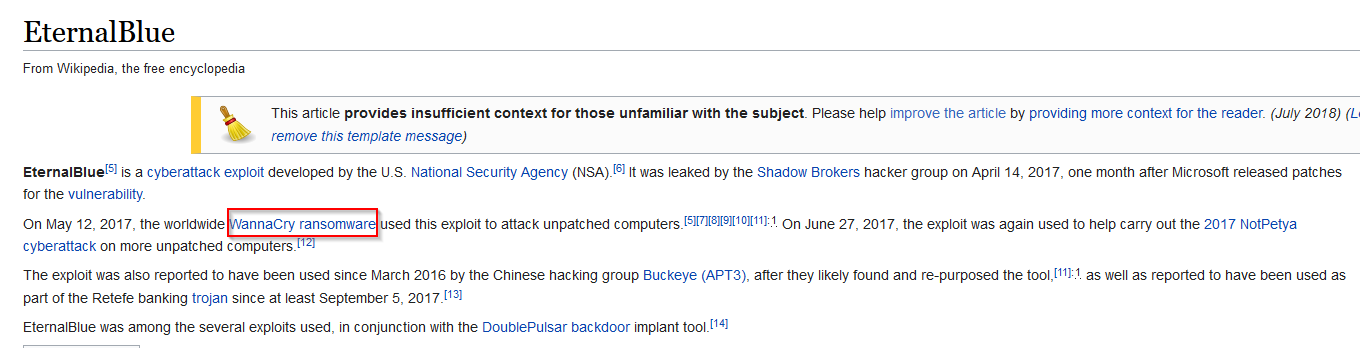
Answer : WannaCry
-
Name the first essential step of a Malware Attack?
Answer : delivery
-
Now name the second essential step of a Malware Attack?
Answer : execution
-
What type of signature is used to classify remnants of infection on a host?
Answer : host-based signatures
-
What is the name of the other classification of signature used after a Malware attack?
Answer : Network-based signatures
-
I understand the two broad categories employed when analysing potential malware!
No Answer.
-
Lets proceed
No Answer.
-
I've logged in!
No Answer.
-
The MD5 Checksum of aws.exe
Right click on the exe file then properties and File Hashes tab.
Answer : D2778164EF643BA8F44CC202EC7EF157
-
The MD5 Checksum of Netlogo.exe
Answer : 59CB421172A89E1E16C11A428326952C
-
The MD5 Checksum of vlc.exe
Answer : 5416BE1B8B04B1681CB39CF0E2CAAD9F
-
Does Virustotal report this MD5 Checksum / file aws.exe as malicious? (Yay/Nay)
Answer : NAY
-
Does Virustotal report this MD5 Checksum / file Netlogo.exe as malicious? (Yay/Nay)
Answer : NAY
-
Does Virustotal report this MD5 Checksum / file vlc.exe as malicious? (Yay/Nay)
Answer : NAY
-
What does PeID propose 1DE9176AD682FF.dll being packed with?
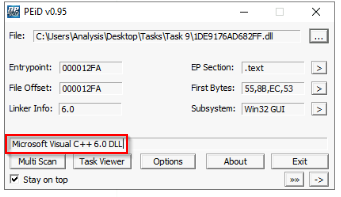
Answer : Microsoft Visual C++ 6.0 DLL
-
What does PeID propose AD29AA1B.bin being packed with?
Answer : Microsoft Visual C++ 6.0
-
What packer does PeID report file "6F431F46547DB2628" to be packed with?
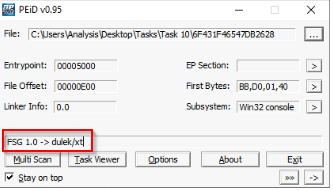
Answer : FSG 1.0 -> dulek/xt
-
Cursed obfuscation!
No Answer.
-
What is the URL that is outputted after using "strings"
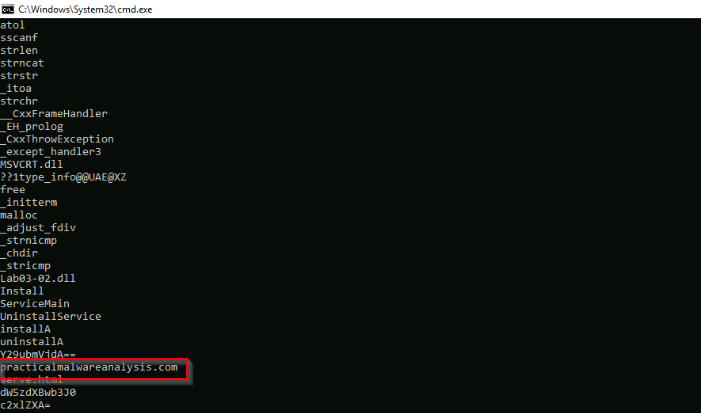
Answer : practicalmalwareanalysis.com
-
How many unique "Imports" are there?
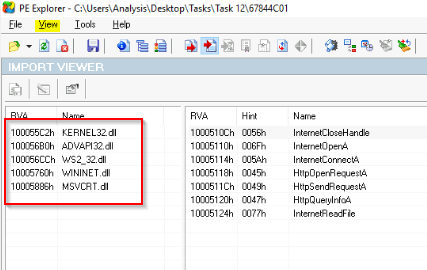
Answer : 5
- How many references are there to the library "msi" in the "Imports" tab of IDA Freeware for "install.exe"
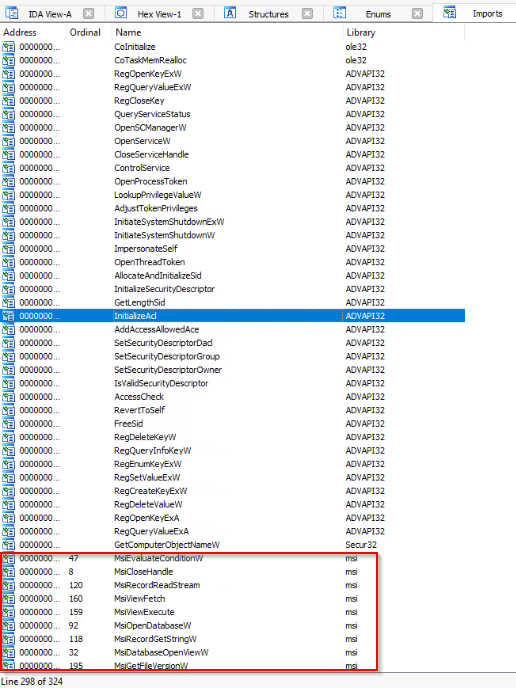
Answer : 9
- What is the MD5 Checksum of the file?
To answer this, click properties of the exe file then go to the file hash tab. You can also use the "md5sum <file>" function in linux terminal if you have access to.
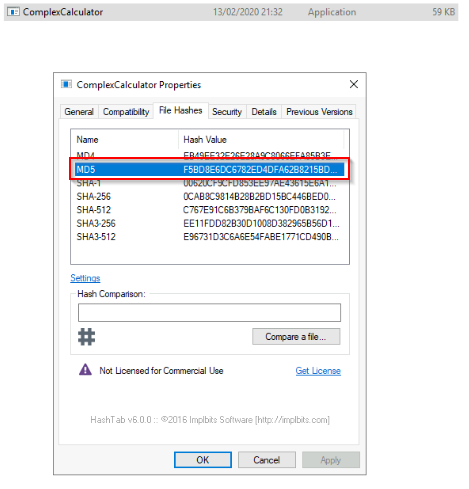
Answer : F5BD8E6DC6782ED4DFA62B8215BDC429
-
Does Virustotal report this file as malicious? (Yay/Nay)
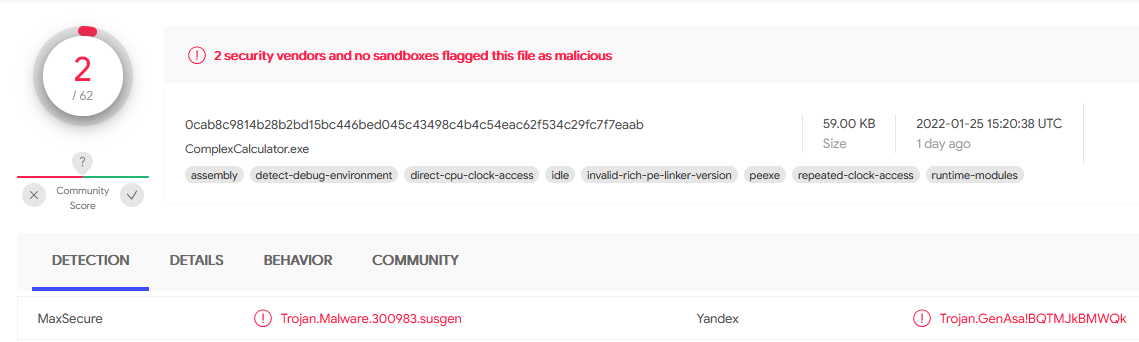
Answer : YAY
-
Output the strings using Sysinternals "strings" tool.
What is the last string outputted?
Open cmd in the folder where sysinternalsSuite String.exe file is then :
strings.exe "C:\Users\Analysis\Desktop\Tasks\Task 14\ComplexCalculator.exe"
[...]
>&>P>_>
?9?H?Q?^?v?
0h1l1p1t1
2 2
d:h:
Answer : d:h:
-
What is the output of PeID when trying to detect what packer is used by the file?

Answer : Nothing found