Red Team Fundamentals
-
Click to continue to the next task
No Answer
-
Would vulnerability assessments prepare us to detect a real attacker on our networks? (Yay/Nay)
Answer : NAY
During a penetration test, are you concerned about being detected by the client? (Yay/Nay)
Answer: NAY
-
Highly organised groups of skilled attackers are nowadays referred to as ...
Answer : Advanced Persistent Threats
-
The goals of a red team engagement will often be referred to as flags or...
Answer : crown jewels
-
During a red team engagement, common methods used by attackers are emulated against the target. Such methods are usually called TTPs. What does TTP stand for?
Answer : Tactics, Techniques and Procedures
-
The main objective of a red team engagement is to detect as many vulnerabilities in as many hosts as possible (Yay/Nay)
Answer : Nay
-
What cell is responsible for the offensive operations of an engagement?
Answer : red cell
-
What cell is the trusted agent considered part of?
Answer : white cell
-
If an adversary deployed Mimikatz on a target machine, where would they be placed in the Lockheed Martin cyber kill chain?
Answer : Installation
-
What technique's purpose is to exploit the target's system to execute code?
Answer : Exploitation
-
Click the "View Site" button and follow the example engagement to get the flag
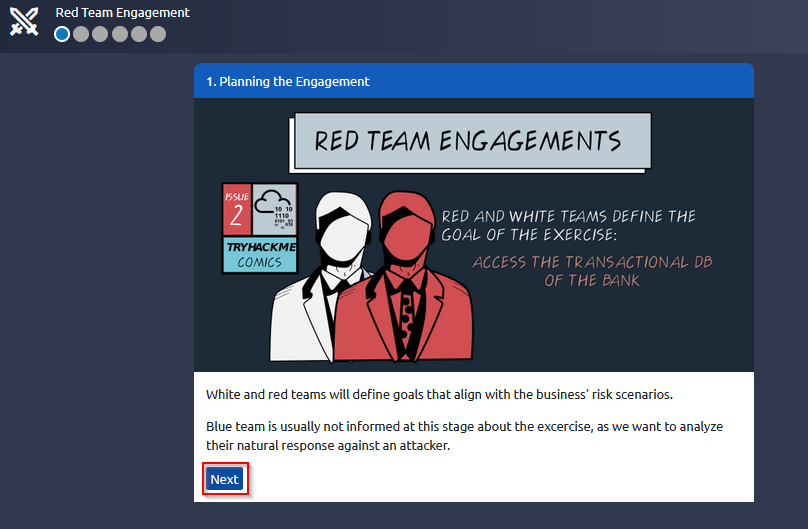
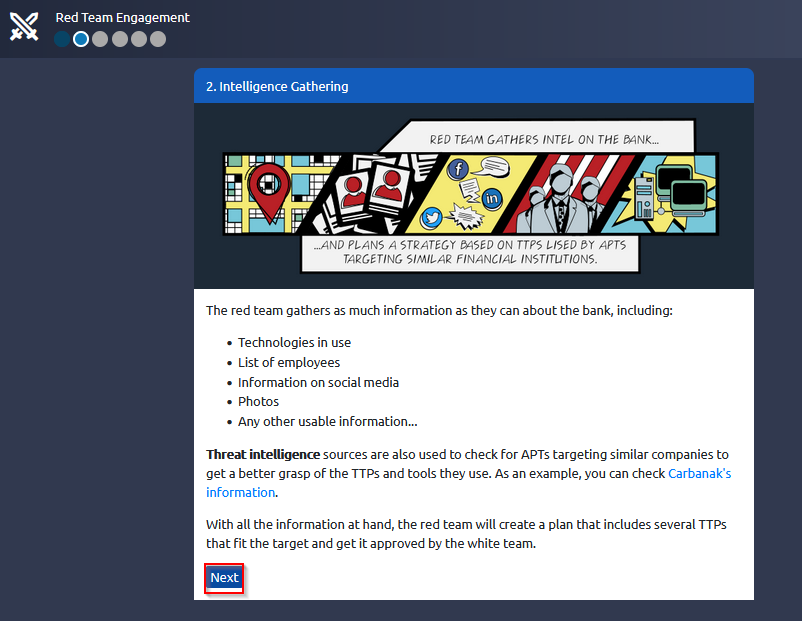
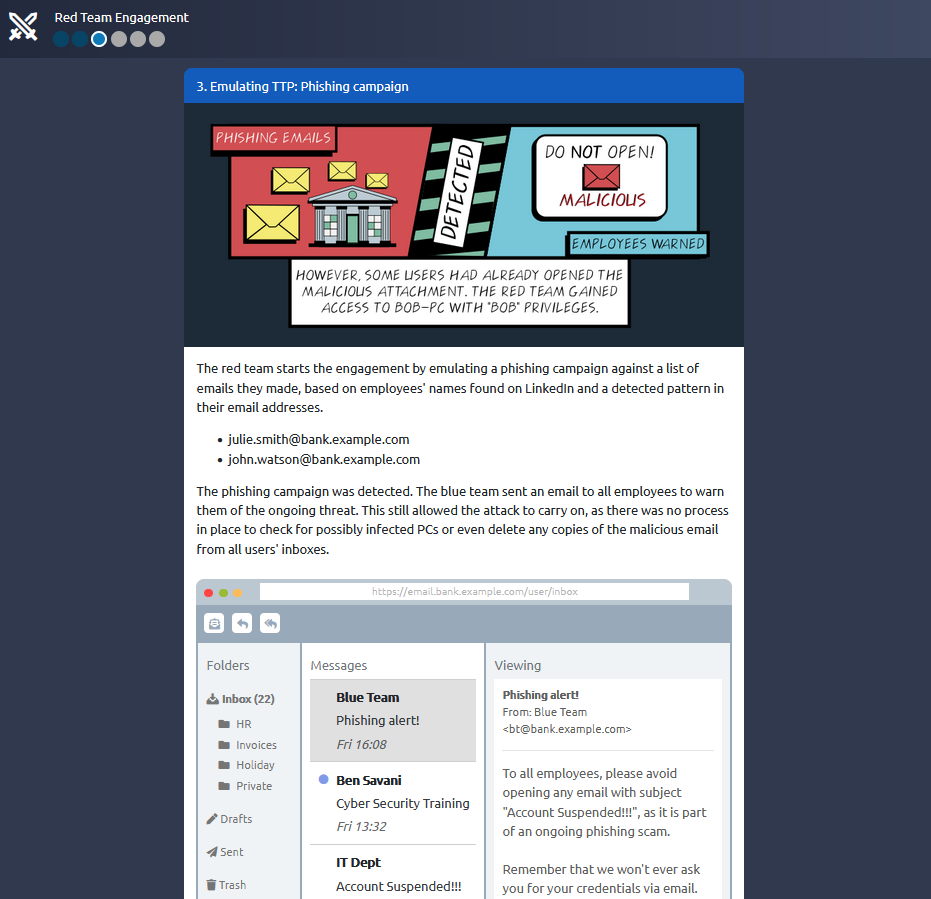

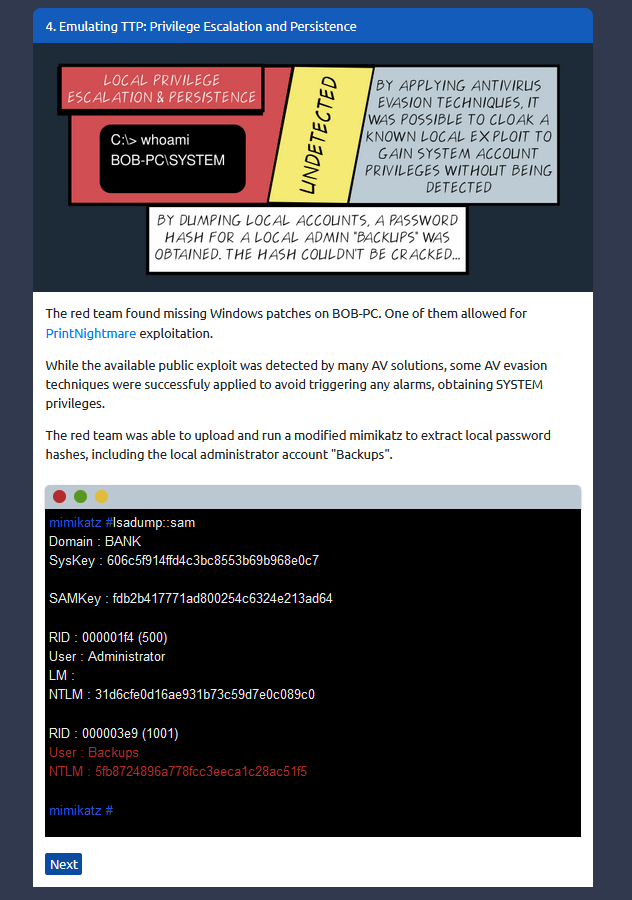
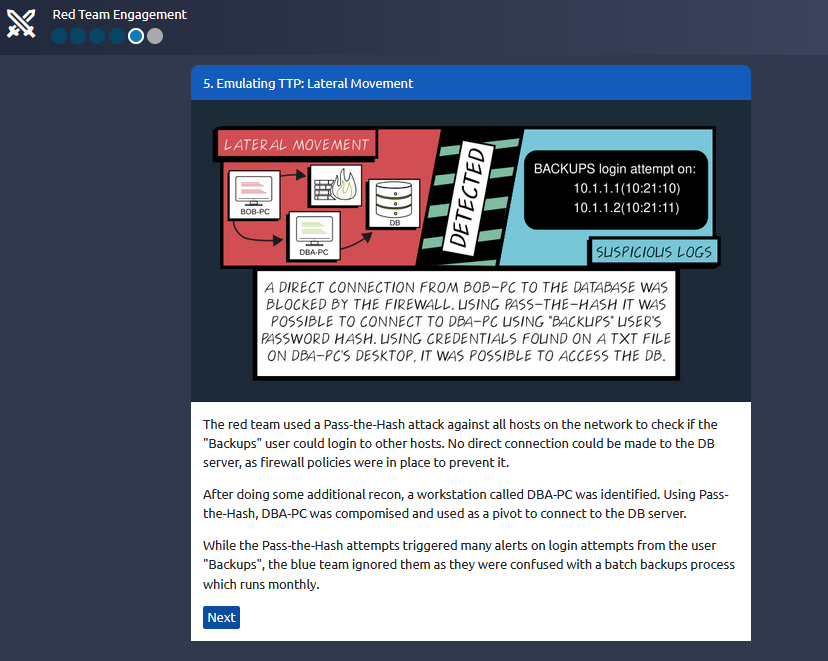
Answer : THM{RED_TEAM_ROCKS}
- Read the above and continue learning!
No Answer.